In an unprecedented move, the author of a piece of ransomware with file encryption routines has released the database with the decryption keys for the data locked on the infected computers and issued an apology.
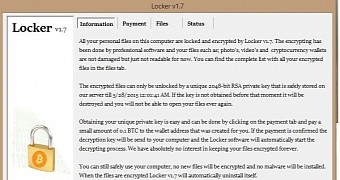
Locker ransomware emerged a while ago and its behavior was marked by strangeness because it did not proceed to encrypt targeted files on compromised computers immediately after installation.
Instead, the crypto-malware entered into sleep mode and initiated its nefarious actions at a scheduled time, set by its author for a particular day (May 25), at midnight, local time.
One possible explanation for acting this way was that the author had not put in place the infrastructure for collecting the ransom money and the automatic delivery of the decryption keys for the paying victims.
Author promises automatic decryption
On Saturday, this theory was debunked by the author, with an apologetic entry on Pastebin, which linked to a CSV (comma-separated values) database hosted by Mega cloud service containing the information to unlock the files on compromised systems.
The author, signing as “Poka BrightMinds,” says that most of the keys in the database were not used and the distribution of new keys has been halted. The CSV file includes 62,703 entries, which would be an indication of the number of systems affected by the malware.
An automatic decryption routine has been scheduled for June 2, at midnight, according to the author of Locker. This way, all trouble created by Locker will be undone, without user intervention.
Distribution channel remains undisclosed
Locker is not as fierce an infection as other crypto-malware, and while it deletes the shadow copies of the files, it does so only for the system drive, allowing data on other partitions to be recovered.
The method for distributing the malware is not known, but some people online say that it may have reached computers via a cracked copy of the Minecraft game, although this has not been confirmed and other victims do not have the game installed, or rely on a genuine copy.
The reasons behind the release of the ransomware tool have not been shared by the author.
 14 DAY TRIAL //
14 DAY TRIAL //