Cybercriminals behind the Asprox botnet seem to pay attention to the researches and blog posts regarding their “business” and to improve their malware in order to avoid detection.
FireEye, a US-based company that provides threat forensics services and protection against advanced cyber-threats, has published a report that informs of the latest developments regarding the phishing campaign carried out through Asprox botnet.
Compared to previous Asprox malicious email campaigns, the new version no longer provides the victim with an URL link in the body of the message but attaches a compressed file containing the payload.
In order to make the victim unload the malicious file, cybercriminals send court-related emails that purport notices of appearance.
According to FireEye, court-request emails seem to be the latest trend in the campaign and the most successful one in the phishing scheme.
The company notes that it recorded the following variations in the email subject: “Urgent court notice,” “Notice to Appear in Court,” “Notice of appearance in court,” “Warrant to appear,” “Pretrial notice,” “Court hearing notice,” “Hearing of your case,” and “Mandatory court appearance.”
A spike in the campaign activity was registered at the end of May, when Asprox was most active even in comparison to other criminal activities carried out by threats monitored by FireEye (Sality, H-worm, Cryptoloker, Mariposa and TDSS).
The geographical distribution of the campaign shows that the areas most targeted are the United States, Saudi Arabia, Canada, France, the United Kingdom, South Korea and Japan.
As far as the industries affected are concerned, there is a wide range, but those that stand out are Energy/Utilities/Petroleum Refining with 39.07%, and the consumer products group and retail with 36.18%.
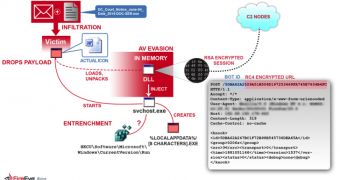
Malware infiltration on the victim’s computer occurs mainly through a phishing email that contains the executable payload under the form of an archived document.
As soon as the host is infected, the threat initiates a svchost.exe process which is then injected with malicious code. Then, once loaded in the memory, it unpacks a DLL and replicates on the machine.
In order to communicate and safely deliver the collected information to the command and control server, the threat employs encryption techniques based on RSA encrypted SSL session (PROV_RSA_FULL), and for the payload RC4 cipher is used.
Furthermore, the attackers seem to use different command and control (C2) nodes for each major campaign, which makes tracking them more difficult.
FireEye’s conclusion is that “each of the Asprox botnet’s malicious email campaigns changes its method of luring victims and C2 domains, as well as the technical details on monthly intervals. And, with each new improvement, it becomes more difficult for traditional security methods to detect certain types of malware.”
 14 DAY TRIAL //
14 DAY TRIAL //