As cybercriminals started to focus their attention on Android users, Google also began to deploy security features to protect the mobile environment from malfeasant activity, managing to decrease installation of potentially harmful apps (PHA) by about 50% in 2014, reveals the first security report for the platform.
The PHA umbrella covers any mobile app that presents a risk to the user. The list includes phishing, device rooting, Trojans, SMS fraud, ransomware, spyware, call fraud, WAP fraud and software that leads to malicious websites.
WAP fraud and ransomware are the latest additions to the list, as 2014 is when they were first detected to affect Android users.
Harmful software affects less than 1% of Androids
The distinction between malignant and benign apps in the Android ecosystem is made by employing several methods, such as signatures, static and dynamic analysis, heuristic and similarity examination, third-party reports, and observation of features that may connect the developer to previously detected PHA.
In the document released on Thursday, Google presents security statistics crunched from billions of data points gathered on a daily basis in 2014.
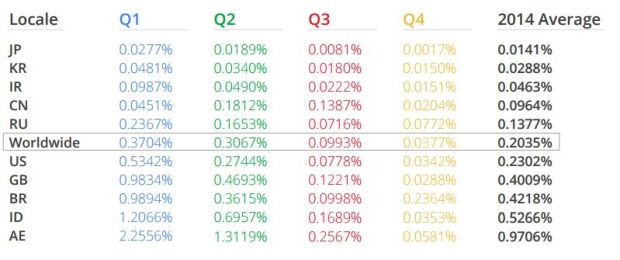
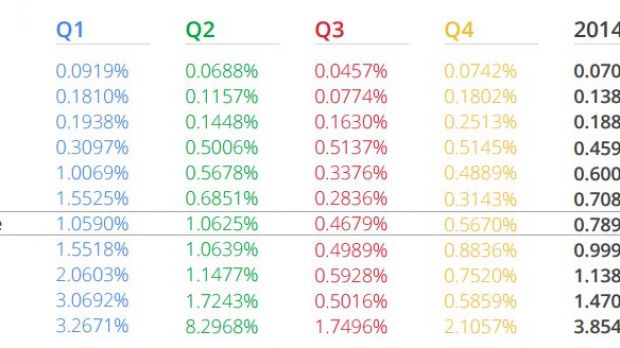
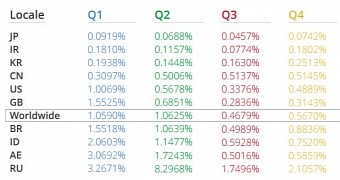
One of the key findings is that less than 1% of Android devices had a PHA installed in 2014 and that fewer than 0.15% of the smartphones installing apps only from Google Play, which protects more than one billion devices, got affected by harmful software.
Security enhancements are highly efficient
The report states that the nearly 50% decrease of known PHA installations was recorded for Android devices outside of Google Play. This was achieved through the Verify Apps feature that relies on the Safety Net service for protection against threats inside and outside Google Play.
Verify Apps is designed to scan the installed apps in order to make sure that their behavior continues to be on the safe side.
Safety Net verifies the configuration of the device and ensures it’s running according to Android’s security expectations. Its monitoring capabilities now cover the ability to detect SSLv3 and other ciphersuite downgrade attacks.
“During October 2014, the lowest level of device hygiene was 99.5% and the highest level was 99.65%, so less than 0.5% of devices had a PHA installed (excluding non-malicious Rooting apps),” according to Google’s statistics.
Apart from Verify Apps and Safety Net service, the company also added reinforcement of Android sandbox via SELinux, a mandatory access control system in the Linux kernel that lowers the exposure of system functionality to applications.
Support for SELinux was introduced in Android 4.3, but subsequent versions expanded its use to enforcing its process isolation capabilities to a specific set of system domains. In Android 5.0, SELinux protection extended to all apps and services on the device.
 14 DAY TRIAL //
14 DAY TRIAL //