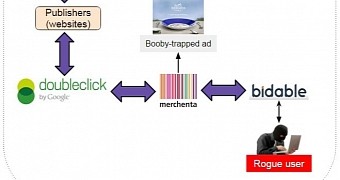
A malvertising campaign carried out through major ad network Merchenta, which distributes online advertisements via Google’s DoubleClick, redirected visitors of compromised websites to locations hosting an exploit kit.
Merchenta was founded with the purpose to deliver personalized ads that would increase revenue by feeding them to relevant users.
The process relies on data collected anonymously, which is analyzed in real time and condensed into patterns based on user behavior, context, promoted product and geographical location of the recipient.
The network is an important player on the US market in particular, touting a monthly reach of 28 billion users in this region alone. In the UK, it delivers content to 14 billion consumers, while in the EMEA space, it has a reach of 18 billion monthly users.
Malicious SWF goes completely undetected
Jerome Segura from Malwarebytes says that the malvertising campaign started when the cybercriminals, clients of real-time bidding (RTB) company Bidable.com, managed to infiltrate the network with a malicious ad that was passed to different mainstream websites via DoubleClick.
“Although DoubleClick is not directly responsible for loading the malicious ad, it starts the chain of trust with the publisher, which unfortunately has little control over the subsequent transactions taking place,” Segura said on Thursday.
According to the researcher, users with outdated versions of Flash were targeted with a malicious SWF file that bypassed the detection of all antivirus products listed on VirusTotal, as data collected at the time of the analysis indicates.
The malware distributed by Flash exploit kit (EK) has not been identified, but it is assumed that it was Cryptowall, as this was delivered in an earlier malvertising campaign that employed the same EK.
Crooks pose as Fortune 500 clients to skip final ad verification
Segura says that one method used by the crooks to bypass checks carried out by ad networks is to pose as an important customer (Fortune 500 company) and submit a legitimate ad in the beginning.
Before the security checks complete and the ad is ready for distribution, the crook submits a malicious version of the ad, claiming that only a minor change has been performed.
To keep the important customer, the ad network does not repeat the assessment and releases the rogue piece into the system.
 14 DAY TRIAL //
14 DAY TRIAL //