Exploits for Adobe Flash Player are delivered by cybercriminals through Nuclear exploit kit (EK) after compromising US-based advertising network MadAdsMedia.
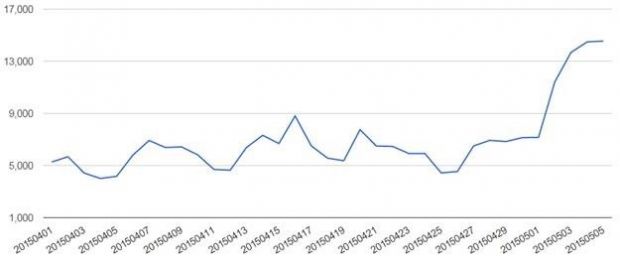
Statistics from Trend Micro claim that up to 12,500 users visiting the websites that serve the malicious advertisements on a daily basis may have been affected by this malvertising campaign.
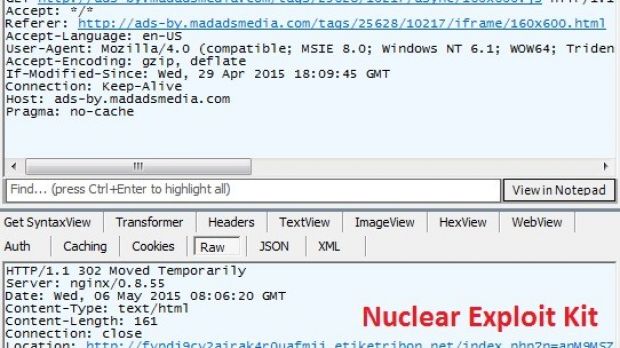
URL in JavaScript points to Nuclear EK
According to the researchers, most of the infections have been identified Japan, the US and Australia. Signs of the attack were first spotted in April, but the traffic levels were relatively low, fraud researcher Joseph Chen says in a blog post on Thursday.
“We initially thought that this was another case of malvertising, but later found evidence that said otherwise. Normal malvertising attacks involve the redirect being triggered from the advertisement payload registered by the attacker. This was not evident in the MadAdsMedia case. What we saw was an anomaly in the URL of their JavaScript library - originally intended to assign what advertisement will be displayed in the client site,” he says.
During the analysis of the malicious activity, it was discovered that in some cases the URL pointed to Nuclear EK, suggesting a compromise of the server MadAdsMedia uses to save the JavaScript library.
Updating to the latest Flash Player avoids infection
Users with unpatched versions of Flash Player are vulnerable to the attack, as the browser-based tool exploits a security flaw (CVE-2015-0359) patched in build 17.0.0.169 of the software. The issue is a double-free vulnerability that can lead to code execution on the affected machine.
It appears that the attackers are delivering a variant of Carberp malware, known for stealing login credentials for bank accounts. However, Chen warns that the payload can be changed by the cybercriminals. The threat can then be anything from ransomware to malware that joins the computer to a network of infected machines.
Users are strongly recommended to apply the latest updates for the software installed on their computer, and especially for browser plugins.
 14 DAY TRIAL //
14 DAY TRIAL //