Kaspersky, the first major antivirus vendor to provide security software specifically aimed at ICS/SCADA equipment, has published a report today that details the sad state of security in the field of Industrial Control Systems (ICS).
The company's experts say that, following an Internet-wide scan, they found 188,019 hosts connected to ICS equipment, in 170 countries around the globe.
Over 170,000 Internet-available ICS devices have vulnerabilities
Of these, 92 percent, or 172,982, contained vulnerabilities that can be exploited to attack, take over, or even harm devices and their normal mode of operation.
While ICS hacking is not as widespread as IoT hacking, which has become a core component of DDoS botnets, malicious groups would find no difficulties in attacking critical infrastructure if they ever chose to.
Cyber-attacks on ICS systems, in general, are at an all-time high, according to a Booz Allen report released in June.
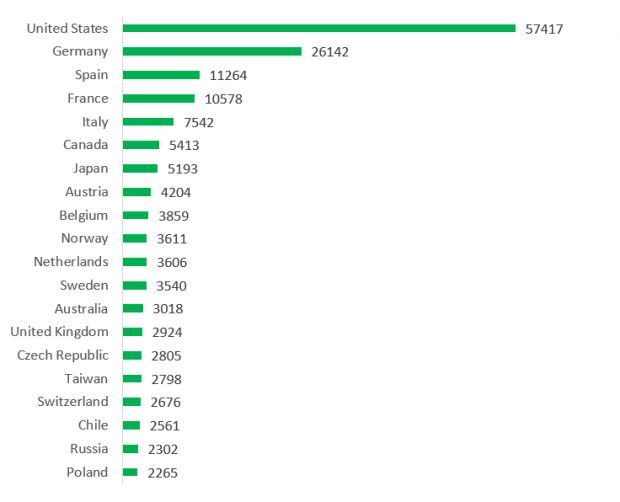
Most of the vulnerable devices are found in the US
According to Kaspersky, most of the vulnerable devices are located in the US (57,417), followed at a long distance by Germany (26,142), Spain (11,264), France (10,578), and Canada (5,413).
Most of these devices are available to external connections via the HTTP protocol (116,900), Telnet (29,586), Niagara Fox (20,622), SNMP (16,752), or Modbux (16,233).
A large number of devices are from vendors such as Tridium (24,446), Siera Wireless (17,908), Beck IPC (14,837), Digi International (12,367), and SMA (11,904).
The vulnerability encountered by far in ICS/SCADA equipment was Sunny WebBox Hard-Coded Credentials (CVE-2015-3964), found in 11,904 devices.
Vulnerable equipment found in all critical industries
The vulnerable devices were found in almost all major critical industries: electricity, aerospace, transportation (including airports), oil and gas, metallurgy, chemical, agriculture, automotive, utilities, drinks and food manufacturing, construction, liquid storage tanks, and smart city technology.
Internet-available and vulnerable devices were found in both the public and the private sectors. Kaspersky experts say that 17,042 ICS components on 13,698 different hosts likely belonged to very large organizations that had failed to properly secure ICS devices.
The high percentage of vulnerable equipment that security researchers discovered shows that companies are failing to update their critical infrastructure in due time, leaving exploitable holes through which malicious actors could carry out economic sabotage.
Vulnerable ICS equipment poses great danger
For public infrastructure, the study shows that nations have failed to learn anything from the Stuxnet debacle, let alone the recent Ukraine power grid attacks.
The large number of countries in which vulnerable ICS equipment was discovered shows that attacks on critical network infrastructure are possible against almost any state around the globe.
"There is no 100 percent guarantee that a particular ICS installation won’t have at least one vulnerable component at any single moment in time," said Andrey Suvorov, Head of Critical Infrastructure Protection, Kaspersky Lab. "However, this doesn’t mean that there is no way to protect a factory, a power plant, or even a block in a smart city from cyber-attacks. Simple awareness of vulnerabilities in the components used inside a particular industrial facility is the basic requirement for security management of the facility."
For more in-depth and technical details, Kaspersky provides two reports, one detailing ICS availability statistics and one ICS vulnerabilities.

 14 DAY TRIAL //
14 DAY TRIAL //