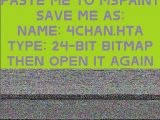
Malware researchers from Microsoft are warning that users are tricked into flooding the 4chan image board by manually executing malicious JavaScript code hidden in an image.
The social engineering attack starts with users receiving a PNG image which displays instructions to copy it in Paint, save it as an HTA file and execute it.
This will cause rogue compressed JavaScript code appended to the PNG file to execute. The code defeats the CAPTCHA test employed by image board and creates bogus topics.
The whole trick relies on the fact that in older versions of Paint files are saved by default as 24-bit Bitmap. Saving the image in this format, regardless of the file name, will decompress the malicious code.
Then saving it as a file with a .HTA (HTML Application) extension and executing it, will cause the actual image information to be ignored and the JavaScript to execute.
"We detect the dropped JavaScript as Trojan:JS/Chafpin.gen!A. We have now seen three versions of this trojan as the malware authors develop their methods," Michael Johnson, a member of the Microsoft Malware Protection Center (MMPC) team, notes.
The 4chan staff is currently trying to fend off the attacks by deleting the flurry of bogus topics created by the malware. However, the threat is not a new one.
The first social engineering attack employing this method dates back to 2008 when users were tricked into saving the code directly as a .JS file and executing it. There have been several mutations since then, with the .HTA one being the latest.
"Here at the MMPC we suggest that you do not follow the instructions of random pictures that you see, especially if the instructions involve altering the file in any way, and then running it. In fact, we would suggest just not running random .HTA files at all," the MMPC researcher advises.
You can follow the editor on Twitter @lconstantin

 14 DAY TRIAL //
14 DAY TRIAL //