The data breach suffered by British Airways which exposed the payment card details of around 380,000 customers appears to be the work of the Magecart cybercriminal group, according to a report from RiskIQ.
After their internal investigation of the hacking incident, British Airways disclosed that both their mobile app and their website were affected, with all payments being impacted for a period of about 16 days, from August 21 to September 5.
RiskIQ detected found out that the Magecart threat group conducted the attack after BA's report mentioned that none of their other services, servers or databases were affected.
This led the security research team to the conclusion that the payment service was the single culprit for the data breach, an area of expertise well-known to Magecart.
The crooks have been known to use web-based card skimmers as the means for stealing credit card payment data, an online version of the classic card skimmers usually hidden by crooks in ATMs and all sorts of other card reading machines.
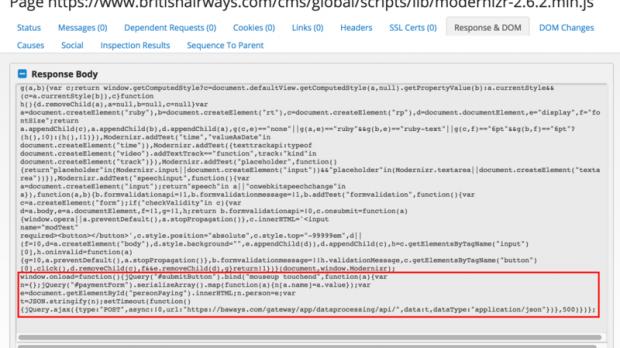
The website and mobile app were breached using the same malicious JavaScript library file
RiskIQ found the incriminating piece of evidence within one of the 50 different JavaScript-based scripts used by British Airways' website to run, namely within the Modernizr library, surreptitiously tucked away at the end of the default content to avoid detection.
Another evident proof of the criminal group messing around with the JavaScript library file was the difference in the timestamp, with the original, untouched version having a December 2012 timestamp, while the version altered by Magecart featured an August 21 one, directly matching the start of the data breach period.
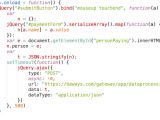
After diving into the code injected by the cybercriminals within BA's website, the RiskIQ researcher found out that a mere 22 lines of JavaScript code were the ones to blame for the data stolen from British Airways' 380,000 customers affected by the hack.
BA's mobile app was also affected by the altered Modernizr JavaScript library because it called on the same script resources used by the website to allow customers to make payments.
"One thing to note is that the magecart actor(s) put in the touchend callback in the skimmer to make it work for mobile visitors as well," said RiskIQ, "which again shows us the high level of planning and attention to detail displayed in this simple yet extremely effective attack.
Magecart - active since 2015 and with successful data breaches of at least two notable targets
The researchers also found out that all stolen data was sent by the threat actors to the baways.com domain on a server located in Romania with the 89.47.162.248 IP address, but owned by a Lithuanian VPS (virtual private server) provider named Time4VPS.
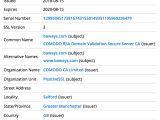
Furthermore, to make the baways.com domain more credible, the crooks used a paid SSL certificate issued by the COMODO CA, instead of going for the free LetsEncrypt version which might have raised some eyebrows when attached to the website of British Airways.
The SSL certificate was issued almost a week before the Modernizr library was injected with the malicious code, pointing to the fact that, although the breach started on August 21, the Magecart threat group had access to some British Airways Internet-connected service long before.
The recent British Airways data breach shows that the Magecart threat actors are still a very active criminal group, known to have started their activity in 2015 and with successful attacks on targets such as Ticketmaster and Inbenta, and with the resources needed to pull cyber heists on a large scale at any time.
 14 DAY TRIAL //
14 DAY TRIAL //