According to Verizon’s recently released 2013 Data Breach Investigation Report, financially motivated cybercrimes and state-affiliated espionage campaigns dominated the 2012 threat landscape. Activists have also left an impression, but the impact of their operations hasn’t recorded any significant modifications.
Verizon has revealed that in 2012, over 47,000 security incidents were reported, 621 data disclosures were confirmed, and 44 million records were compromised. If we look at the figures for the last nine years, the number of compromised records has reached around 1.1 billion.
Financially-driven criminals clearly dominated the security landscape last year, 75% of breaches falling into this category. However, state-affiliated groups rose to the number two spot.
The company believes there are a couple of main reasons for which the number of espionage attacks – which target classified information, trade secrets and technical resources – has increased.
“On one hand, we saw a dip in financially motivated cases against small organizations in our dataset, and that dip allows other trends to become more pronounced. Another factor is the larger set of data sharing partners in this report that widens the population of incidents we can analyze,” the report reads.
“Furthermore, our own investigations comprised more espionage cases than any previous year, and this was bolstered by increased efforts to collect, share, and correlate IOCs that greatly improve the ability to uncover targeted attacks.”
So where do attacks come from?
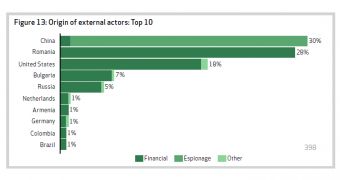
The attackers are distributed across 40 different nations. Most of the financially-driven actors come from the US, Romania, Bulgaria and Russia.
As far as espionage is concerned, it probably doesn’t surprise anyone that the country of origin has been China in 96% of cases.
This could mean two things: China is really the most active source of national and industrial espionage in the world, and that other state groups might be more capable when it comes to hiding their tracks.
The complete 2013 Data Breach Investigations Report is available for download here.
 14 DAY TRIAL //
14 DAY TRIAL //