Researchers are tracking a group of cybercriminals in Brazil that created malware relying on the man-in-the-browser technique to compromise 495,753 “boleto” transactions.
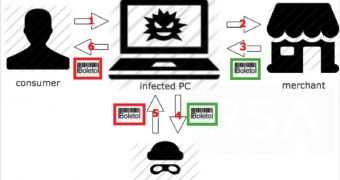
The term “boleto” may not ring any bell to most of us, but in Brazil it is a very popular payment instrument that can be used in online purchases through the emitting bank’s website. One particularity is that boleto transactions can only be reversed by bank transfer.
The popularity of boletos is significant, being the second most used form of payment in Brazil. As such, it is easy to understand the interest cybercrime groups have in boleto transactions.
Detected as Eupudus by some antivirus software, the malware was spotted in the wild towards the end of 2012. It is designed to hook into the web browser (Google Chrome, Internet Explorer, Mozilla Firefox) and disable its security mechanisms on the fly, allowing it manipulation of secure transactions, despite the authentication factors in effect.
Security researchers at RSA, who refer to the malware under the name of “Bolware,” say that the Brazilian banks have put in great effort to thwart its actions since its discovery, but the crooks have modified the malware to counter the defense mechanism.
The total value of boleto transactions intercepted by the criminal group is estimated at $3.75 billion/€2,755 billion in two years’ activity, based on 8,095 boleto IDs. However, this isn’t the amount that criminals cashed in because the number of boletos paid by the victims is not known.
Based on the number of unique addresses, the researchers have found that the number of computers compromised by Bolware amounts to 192,227. Their investigation has also revealed that the malware managed to collect a total of 83,506 email credentials. The number of bank brands affected by the operation is 34.
“Boleto malware is a major fraud operation and a serious cybercrime threat to banks, merchants and banking customers in Brazil. While the Bolware fraud ring may not be as far-reaching as some larger international cybercrime operations, it does appear to be an extremely lucrative venture for its masterminds,” Eli Marcus writes for RSA.
The Bolware investigation is ongoing, and RSA works with Brazilian banks to develop and implement various mitigation methods against the malware.
“While the Boleto malware and the manner in which it modifies Boleto transactions is difficult to detect, it appears to affect only Boletos that are generated or paid online via infected Windows-based PCs using three popular web browsers,” says Marcus.
It appears that government-issued boletos, which are used for paying taxes and municipal fees, are not affected by the operation. A safe alternative for commercial transactions appears to be the use of boletos via mobile applications or digital wallets.
 14 DAY TRIAL //
14 DAY TRIAL //