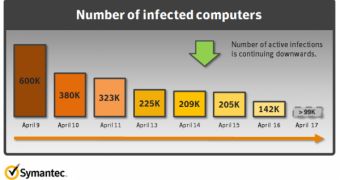
Security software vendor Symantec has released a “quick follow up” to the OSX.Flashback.K issue confirming that, of the 600,000 infected Macs, 140,000 remain affected by the Flashback Trojan.
The statistics from Symantec’s sinkhole indicate a declining number of infected Macs by the passing of each day.
“However,” Symantec says, “we had originally believed that we would have seen a greater decline in infections at this point in time, but this has proven not to be the case."
"Currently, it appears that the number of infected computers has tapered off, but remains around the 140,000 mark.”
The firm believes the infection numbers should have dramatically decreased by now, “as there have been tools released by Symantec and other vendors in the past few days concerning this threat.”
Symantec’s advice is to “install the latest patches, ensure that your antivirus is up to date with the latest signatures, and to use the free Norton Flashback Detection and Removal Tool,” if you suspect that your Mac has been infected with the Flashback Trojan.
It is noted in Symantec’s report that the Flashback payload is considerably larger than the initial stage downloading component.
They’re still analyzing the issue, and they’ve discovered a new feature of the Trojan - “it can now retrieve updated C&C locations through Twitter posts by searching for specific hashtags generated by the OSX.Flashback.K hashtag algorithm.”
The firm acknowledges that another Mac threat is leveraging the recent Oracle Java SE Remote Java Runtime Environment Denial Of Service Vulnerability used to distribute the Flashback Trojan.
That threat is OSX.Sabpab (or OSX.Sabpub as some reports refer to it), which we discussed yesterday.
“OSX.Sabpab has also been seen in targeted attacks distributed with malicious Word documents exploiting the Microsoft Word Record Parsing Buffer Overflow Vulnerability (CVE-2009-0565, BID 35190),” reads Symantec’s post.
The company believes “it is paramount that you have the latest antivirus signatures installed and have applied the latest available patches for both the operating system and third-party applications.”
 14 DAY TRIAL //
14 DAY TRIAL //