Baidu, a Chinese search engine, is offering an SDK (software development kit), which, according to Trend Micro researchers, includes functionality that can be abused to install backdoors on users' devices.
The SDK in question goes under the name of Moplus, and according to recent estimates, it has been included in 14,112 Android applications, of which 4,014 are developed by Baidu itself. Putting all the download figures for these apps together, over 100 million Android users may be in danger.
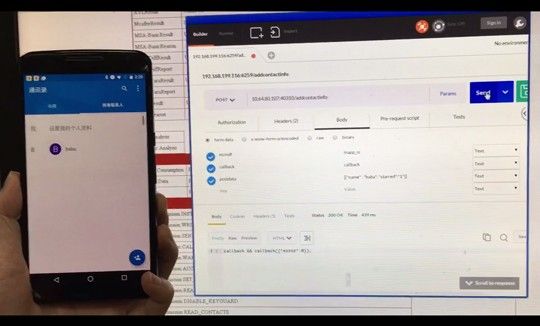
The SDK listens to commands coming via HTTP requests
According to Trend Micro, the Moplus SDK automatically launches an HTTP server on the user's smartphone, which can work silently, in the phone's background, without the user ever noticing it.
This server can be controlled by attackers, who can send it HTTP requests on a particular port, telling it to execute malicious commands. Right now, Trend Micro has detected the SDK using the port 6259 or 40310.
These are a few of the scariest things the Moplus SDK can do:
- get phone details
- send SMS messages
- make phone calls
- add new contacts
- download files on the device
- upload files from the device
- get a list of local apps
- silently install other apps (if the device is rooted)
- push Web pages
- get phone's geolocation, and more.
Since the SDK automatically deploys the Web server when an app that includes the Moplus SDK is started, attackers only need to scan a mobile network for the two ports and find vulnerable devices they can abuse.
Trend Micro observed the SDK being used by at least one malware strain in the wild (ANDROIDOS_WORMHOLE.HRXA).
Thieving SDKs, a new trend among Chinese companies
Baidu was told of this issue and removed some of the SDK's functionality, but not all. In their most recent update, Baidu eliminated the SDK's ability to download or upload files, scan for local apps, add new contacts, or scan downloaded files. All of the other functionality was left intact.
This is not the first malicious SDK we see from a Chinese company, having previously reported on another case that involved the Taomike SDK, which was secretly stealing SMS messages from Android devices and uploading them to a server in China.
The same functionality was also found in another SDK developed by Youmi, but that incident affected only 256 iOS apps, which Apple eventually banned from the App Store until they removed the aforementioned SDk's code.
 14 DAY TRIAL //
14 DAY TRIAL //