- By Catalin Cimpanu
- November 24th, 2015

ModPOS Is a Sophisticated Criminal Malware Framework Targeting POS Devices
ModPOS was active since late 2013, currently undetected
- By Catalin Cimpanu
- November 24th, 2015
Adult Apps on Android Might Be Harboring Ransomware, Scareware and SMS Trojans
Security pros recommend that users stay away from smut
- By Catalin Cimpanu
- November 23rd, 2015

Adware Uses Certificates & Windows UAC to Block Antivirus Installations
Vonteera adware is re-classified as a full trojan
- By Catalin Cimpanu
- November 18th, 2015

Linux.Encoder.1 Ransomware Has an Older Brother, Just as Dumb
Researchers uncover a predecessor for Linux.Encoder.1
- By Catalin Cimpanu
- November 14th, 2015

PoS Malware Spread via Weaponized Microsoft Word Documents
Distributed via Word files and the Angler EK
- By Catalin Cimpanu
- November 11th, 2015
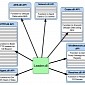
Kaspersky and Microsoft Security Products Abused to Install Spying Trojan
Bookworm trojan can be used to spy on infected victims
- By Catalin Cimpanu
- November 6th, 2015

Ransomware Found Targeting Linux Servers and Coding Repositories
Malware operators are taking aim at Web developers
- By Catalin Cimpanu
- November 6th, 2015

Epic Fail: Power Worm Ransomware Accidentally Destroys Victim's Data During Encryption
Stupid ransomware throws away the encryption key
- By Catalin Cimpanu
- November 5th, 2015

Evildoers Rejoice: CryptoWall Ransomware Version 4.0 Is Here
CryptoWall 4.0 comes with more annoying ransom notes
- By Catalin Cimpanu
- November 4th, 2015

Researchers Discover Powerful Encryption-Capable Ransomware That Works Offline
"Offline" ransomware discovered, has the capabilities and encryption powers of online, C&C-controlled ransomware
- By Catalin Cimpanu
- November 4th, 2015

Adware That Roots Android Devices Found in 20,000 Apps
Android users plagued by uninstallable adware
- By Catalin Cimpanu
- November 2nd, 2015

Chimera Ransomware Threatens to Publish Personal Files
Ransomware authors scare victims by telling them they will publish their personal files and photos online
- By Catalin Cimpanu
- October 22nd, 2015

New Ransomware Infects Computers via Windows Remote Desktop Services
There are some ways to go around the malware's file encryption and recover at least some sensitive files
- By Catalin Cimpanu
- October 20th, 2015
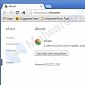
Malware Disguises as Google Chrome Browser Clone
eFast browser poses as Chrome but inserts unwanted ads
- By Catalin Cimpanu
- October 9th, 2015

Undetectable Moker RAT Targets Windows-Based Corporate Networks
Moker remote access trojan comes with anti-sandboxing features, VM evasion, and screenshot capabilities
- By Catalin Cimpanu
- October 6th, 2015

HDRoot Bootkit Impersonates Microsoft's Net Command
HDRoot is the work of the Winnti APT group
- By Catalin Cimpanu
- October 5th, 2015
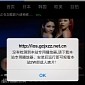
YiSpecter, the First iOS Malware That Attacks Non-Jailbroken Devices
The malware spreads with the help of an adult movie player