Automattic, the company behind WordPress, has fixed a stored XSS vulnerability in its Akismet spam fighting plugin, which would have permitted attackers to compromise WordPress sites.
Akismet is a plugin that comes bundled with all WordPress installations by default, being employed on millions and millions of WP sites.
The plugin is incredibly useful, allowing site administrators to easily detect comment spam and have it cleaned from the site or marked for review in a special section inside the WordPress administration panel (the Comments section).
Akismet versions 3.1.4 and lower are all vulnerable
According to Sucuri, a security vendor specialized in WordPress protection systems, a flaw exists in the Akismet plugin that affects all versions up to and including 3.1.4.
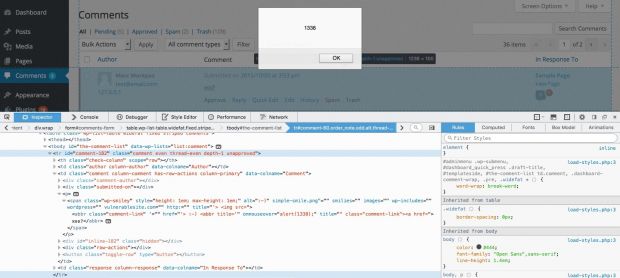
This flaw allows attackers to insert malicious code via blog comments, which gets stored inside the website's database, and then gets executed every time the administrator hovers over malformed links in the site's backend Comments section.
Despite the plethora of XSS protection filters WordPress comes built with, the flaw manifests itself due to a series of bad conjunctions, and only when the website is configured to transform text-based smileys like ":)" into graphic emojis.
Since this feature is turned on by default in all WordPress sites, along with the possibility of posting comments, the attackers have a very large target at hand.
Automattic fixes bug and also protects vulnerable Akismet plugin versions (in the cloud)
The bug was discovered at the start of the month, and Automattic patched it in less than two weeks, releasing version 3.1.5 to fix the issue.
Additionally, because Akismet checks all comments for spam against its cloud-based servers, it is also able to detect API calls coming from older Akismet plugin versions.
This allowed the WordPress team to set up a protection system in place that blocks attacks of this type, even if the webmaster has not yet upgraded their local Akismet plugin.
Earlier this month, the same Sucuri team uncovered a similar stored XSS flaw in another of Automattic's plugins, Jetpack.

 14 DAY TRIAL //
14 DAY TRIAL //