Sucuri, a cyber-security vendor who offers a suite of services, including WordPress security, has found a persistent XSS (cross-site scripting) flaw in one of the most popular WordPress plugins, Automattic's own Jetpack plugin.
Jetpack is a WordPress plugin developed by Automattic, the company that runs WordPress.com and also supervises the development of the WordPress open source CMS.
The plugin integrates various features found in the WordPress.com dashboard into the administrative panel of the WordPress open source platform.
Jetpack has been of great use to webmasters in the past, allowing them to customize their site using one single plugin, instead of having to install tens of smaller add-ons that do the exact same thing.
Jetpack has more than 1 million downloads, and its code is managed by Automattic's own development team.
During their regular research of popular WordPress plugins, Marc-Alexandre Montpas from Sucuri was able to discover a problem with the way email addresses are sanitized in the Jetpack contact form module.
This module lets webmasters add a contact form to any page or post, using a button added to the native WordPress WYSIWYG editor.
XSS bug affects Jetpack 3.7 and lower, is fixed in 3.7.1
This vulnerability affected Jetpack versions 3.7 and prior, and according to Sucuri, it was remotely exploitable, did not require a high-level of technical knowledge, and scored 8 out of 10 in their vulnerability DREAD severity system.
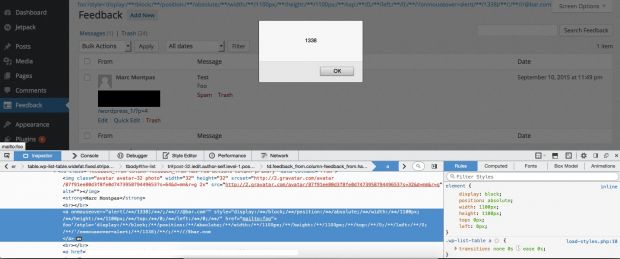
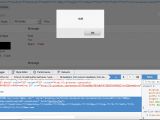
To take advantage of this XSS bug, an attacker could have crafted a malicious email string which, when submitted, would have ended up in WordPress' database.
Whenever a WP administrator would go to the Feedback section of their admin panel, the email string would be executed, allowing the attacker to run malicious code inside the WordPress backend.
"The attacker could use this bug and a bit of web browser hackery [...] to do whatever they wants with the site (hiding a backdoor for future exploitation of the hacked site, injecting SEO spam, etc.)," says Mr. Montpas.
Sucuri reported its findings to Automattic on September 10, and the dev team fixed the XSS bug in Jetpack 3.7.1.
 14 DAY TRIAL //
14 DAY TRIAL //