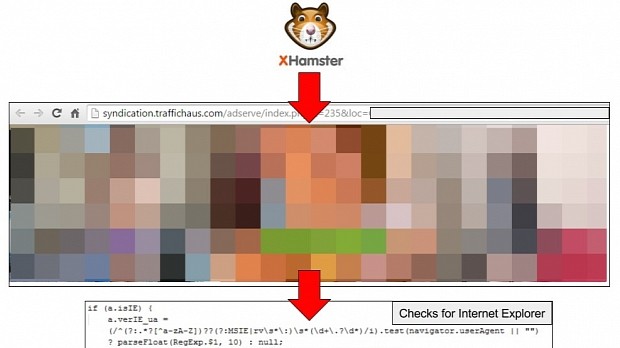
A malvertising campaign that's been seen raging on the Internet since August is now affecting visitors of xHamster, a top free adult video portal.
The campaign has been coming and going out of the limelight, affecting not only smaller sites but also big industry names like Yahoo, MSN, eBay, eHow, Answers.com, and Wowhead, the biggest World of Warcraft online database.
All malvertisements served through this campaign seem to follow the same pattern, infecting users with the help of an exploit kit, after previously passing their connection through a series of encrypted browser redirections, with most of the malicious code hosted on free cloud hosting accounts.
The campaign hosts code on IBM's Bluemix cloud
According to Malwarebytes, the security company that's been tracking and reporting on the campaign since its beginning, this time around, the malvertising campaign seems to be using IBM's Bluemix cloud hosting system, which offers HTTPS support to all users on their free plan.
This allows attackers to disguise their traffic and work without being easily detected by firewalls and online threat detection systems.
The most recent campaign that is affecting xHamster's users is being spread by an ad for the Sex Messenger dating app, served by online advertising company TrafficHaus.
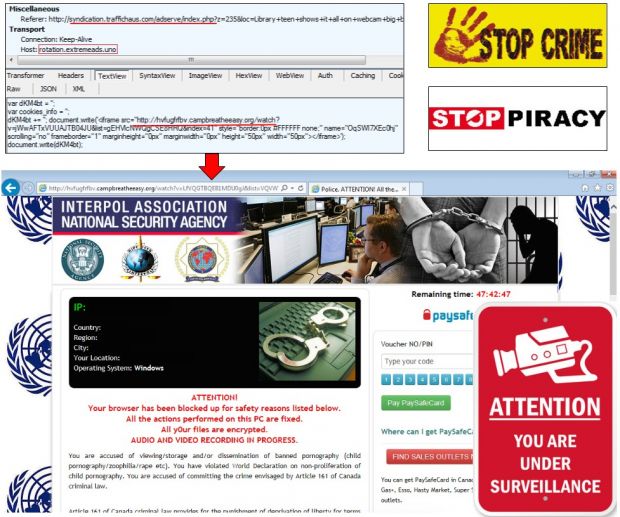
As Malwarebytes explains, the malicious ad redirects users via an IBM Bluemix account to a landing page serving the Angler Exploit Kit, where the user is infected with malware. In some instances, the browlock (browser) ransomware has also been served.
Attackers are using an IE vulnerability to detect traffic coming from real users
Unlike its previous iterations, the malvertising campaign now includes pre-Angler checks, executed during one of the redirection stages, when the attackers check for the presence of Internet Explorer.
Attackers are particularly checking for the XMLDOM vulnerability in IE (CVE-2013-7331), which allows them to detect if the user's computer is running a virtual machine or malware reverse engineering tools.
This allows them to distinguish from security sandbox and honeypot environments and only redirect users to the final Angler page if the checks deem the traffic as coming from a real person.
Malwarebytes reported the campaign to TrafficHaus, which has taken the necessary steps to have the malicious ad taken down.

 14 DAY TRIAL //
14 DAY TRIAL //