During the past days, the crooks behind the Locky ransomware have amped up their operations and distributed hundreds of thousands of spam emails that contain malicious files, which, when opened, would install a new version of the Locky ransomware that can work without an Internet connection.
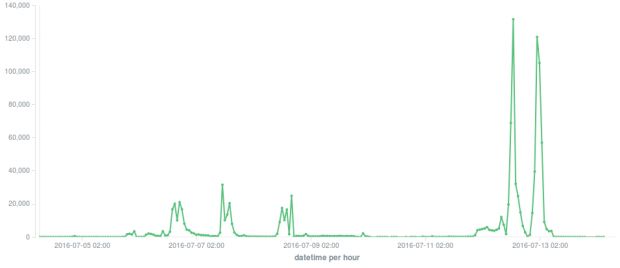
Finnish security firm F-Secure observed the campaign and pointed out that, on July 12, the group behind this ransomware sent out a whopping 120,000 spam email messages every hour in two massive surges of activity.
As with past Locky campaigns, these files were ZIP archives that contained a JavaScript file, which, when executed, installed the Locky ransomware.
New Locky version appears on the same day as the spam surge
According to German security vendor Avira, its researchers stumbled upon a new Locky version that can work in "offline mode."
Avira's experts said they detected this new variant on July 12, the same day when the spam surge happened, but they reported independently of F-Secure, so it is not officially confirmed that the spam wave delivered the new variant, even if all clues point to it.
This new Locky version is very different from past Locky variants, which needed an Internet connection to start the encryption process. Because of this, network administrators discovered that, by shutting down Internet access to a company when they detected one Locky infection, they could also stop subsequent computers from being compromised.
New Locky version uses a much simpler encryption scheme
Locky's authors seem to have addressed this issue and have now created a variant that can work around this limitation, albeit using a weaker encryption method.
"That [speaking of Locky's offline mode] makes it tougher to block," said Avira's Lyle Frink. "But, this new variant may have the weakness that once someone has paid the ransom for their private key ID - it should be possible to reuse the same key for other victims with the same public key."
This comes in handy to corporate environments, where Locky's authors are known to ask for more money than usual, just because they managed to infect a computer holding more precious data.
Victims can pull the computer from the enterprise network, reinfect it, pay the ransom, and then use the decrypter to recover the files at a lower price.
This is possible because the Locky offline version generates the same ID per computer, unlike its online version that generates different IDs per infection, not per computer.

 14 DAY TRIAL //
14 DAY TRIAL //