Security researchers from multiple companies have detected an aggressive campaign that's spreading a new ransomware family via Dridex's traditional infrastructure.
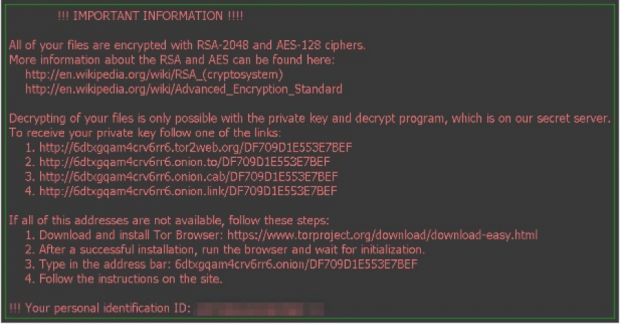
Named Locky because it uses the .locky extension to rename all encrypted files, this new ransomware family is spread via weaponized Word files.
"There is a link between the Dridex botnet affiliate 220 and Locky due to similar styles of distribution, overlapping filenames, and an absence of campaigns from this particularly aggressive affiliate coinciding with the initial emergence of Locky," Palo Alto researchers explain.
There's a connection between the Dridex banking trojan and Locky
Researchers go on to point out that the weaponized Word files use intermediary malware called the Bartallex downloader. This malware is downloaded by the Word document after users enable macros support in their Office suite, and its role is to download the final payload.
In this particular case, it was the Locky ransomware, but most of the times, Bartallex has been associated with the distribution of the Dridex banking trojan.
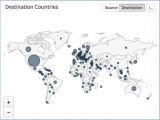
Using telemetry data from their honeypots and security endpoint software, Palo Alto reports that over 446,000 Bartallex instances tried to download the Locky ransomware, but this number could be much higher.
Taking into account that there's a 50% chance of users opening email spam, that 1% of ransomware victims end up paying the ransom, and that Locky operators ask for 0.5 Bitcoin ($200 / €180), Palo Alto researchers say that the group behind this campaign could have made several hundred thousands of dollars if their software hadn't blocked those Bartallex instances.
Locky ransomware goes after your unmapped drives
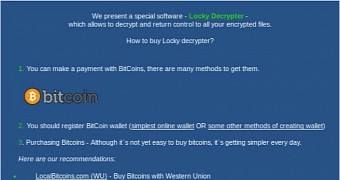
As for the ransomware's technical abilities, researchers from Bleeping Computer say that Locky is uncrackable and borrows many techniques from CryptoWall, the most efficient & lucrative ransomware family of all time.
What's unique to Locky, compared to CryptoWall, is its ability to scan for unmapped network drives and encrypt those as well. This functionality had only been seen before in the DMA Locker family, discovered two weeks ago.
What this means is that if you have a backup drive connected to your computer network, even if you tell Windows to "forget" about it by unmapping it, as long as it's still physically attached to the network/PC, it's still in danger.
I guess someone figured out #Ransomware pays better than #Dridex? Huge run of #Locky killed by @invincea pic.twitter.com/XGgO6r4qxs — Cyber Mad Hatter (@BelchSpeak) February 16, 2016
Just received a sample of the new #ransomware calling itself #Locky. #malware pic.twitter.com/daJSss8OHz — Paul Burbage (@hexlax) February 16, 2016
 14 DAY TRIAL //
14 DAY TRIAL //