The issue with legitimate apps being replaced by rogue ones on iOS has attracted enough attention to cause an alert from the US-CERT (Computer Emergency Readiness Team).
This was to be expected, considering the fact that the operating system versions affected by the issue, dubbed Masque Attack, are those with the largest market share (iOS 7.1.1, 7.1.2, 8.0, 8.1, and 8.1.1 beta), being installed on 95% of the devices.
Not checking digital certificates is at the root of the issue
The attack relies on the lack of a security check in Apple’s operating system for mobiles as far as the certificate of apps with the same bundle identifier is concerned.
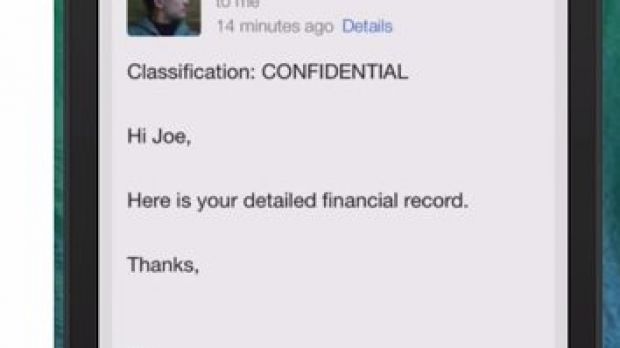
Discovered by researchers at FireEye and reported to Apple on July 26, the abuse consists in tricking the user into installing a malicious app signed with an enterprise certificate that impersonates a legitimate one, both having the same bundle ID but different signatures.
A bundle ID is used in iOS and OS X to recognize the availability of the app updates and it is a unique string, generally output in reverse DNS notation (e.g.: com.google.Gmail).
The severity of such an attack is increased by the fact that the malicious app not only completely replaces and impersonates the looks of the original one but it also uses the user information, thus making the impersonation completely undetectable.
Limited form of Masque Attack used by WireLurker
In an advisory on Thursday, US-CERT warns that this technique allows a threat actor to mimic the original app’s login interface to steal the victim’s account credentials, access sensitive information from local data caches, run background monitoring of the activity on the device, and even gain root privileges on the device. Moreover, the replacement of the genuine app does not offer any visible sign.
It appears that the report of such an issue has triggered a response from Apple, who said that they were not aware about customers being affected by the Masque Attack.
However, even if they do not have any evidence of such incidents in the wild, security FireEye researchers said that after taking a look at WireLurker, a malware that infects iOS devices via a USB connection to OS X or Windows, they found that it started to rely on a limited form of Masque Attack.
WireLurker, discovered by Palo Alto Networks, is believed to have affected hundreds of thousands of iOS users in China. Its operators uploaded trojanized apps to a third-party store (Maiyadi) that provides premium pirated content.
After being installed by the user, the threat waits for an iOS device to connect via USB and then infects the legitimate apps on the phone or tablet by repackaging them on jailbroken gadgets or by adding digitally signed ones on non-jailbroken devices.
To avoid both a Masque Attack and WireLurker, the recommendation is to install items only from official sources such as Apple’s store or a trusted organization.
The Masque Attack demo from FireEye researchers:
 14 DAY TRIAL //
14 DAY TRIAL //