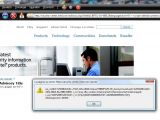
A cross-site scripting flaw affecting the Intel Product Security Center website has been disclosed. Successful exploitation allows for rogue iframe injection, arbitrary redirection and session cookie hijacking.
The Intel Security Center is home to advisories regarding security issues that affect Intel products. "Intel is focused on improving the security of our customers computing environments. We are committed to rapidly addressing issues as they arise, and providing recommendations through security advisories and security notices," a message on the website's main page notes.
The XSS weakness on http://security-center.intel.com has been discovered by a hacker going by the nickname of Methodman. The flaw seems to affect all advisory pages and can be used by ill-intentioned individuals to distribute malware, launch phishing campaigns, or instrument various malicious attacks.
The proof-of-concept code and screenshots published by Methodman demonstrate how poor URL validation allows an attacker to inject an arbitrary iframe or trigger a redirection to another link. In addition, revealing session cookies or launching rogue alerts is also possible. At the time this article was being writtten, the flaws were still active.
Methodman is a member of a group calling itself ']['€AM€LiT€ (Team Elite), which runs a chat network using both the IRC and the NMDC (NeoModus Direct Connect) protocols. The team members describe themselves as programming and security enthusiasts.
The hacker has recently released similar cross-site scripting and SQL injection vulnerabilities affecting the websites operated by several antivirus vendors like Kaspersky, Avira, ESET, F-Secure and Bitdefender. According to his own account, he was inspired to probe the security of antivirus sites by the similar acts of a Romanian white-hat hacking group called HackersBlog.
The security researchers from Kaspersky claim that cross-site scripting flaws are not very dangerous. "Kaspersky Lab’s security experts rate XSS weaknesses as low risk because a large number of conditions have to be met before it can affect users," a company official explains as part of a response to a request for comment submitted by Softpedia.
From a technical point of view, such weaknesses might indeed be of low risk, however, the nature of the websites they affect can make a lot of difference as far as the impact they have is concerned. Cyber-criminals constantly make use of social engineering techniques to lure users into visiting malicious pages.
Sometimes, they make great efforts to masquerade the links so as to appear that the pages are hosted on popular and generally-trusted websites, like the Intel Security Center is. Therefore, having the possibility to actually inject their rogue code into valid, legit pages is a great advantage for them and increases the credibility of their schemes.
Note: We have contacted Intel regarding this issue and we are awaiting its reply. Keep an eye on this page for a future update.
Update: An Intel spokesperson responded to our inqury and pointed out that "major websites can be subject to these attempts." He also noted that "We continuously defend and monitor for this kind of thing and take corrective action where necessary."

 14 DAY TRIAL //
14 DAY TRIAL //