After the author of Locker crypto-malware released the decryption keys in what can be classified as an act of remorse, a decryption tool is now available for users hit by the ransomware who still need help unlocking the data.
Locker’s behavior was atypical from the start, as it infected computers and then laid dormant on the system, awaiting a wake-up time to begin encrypting files. Its author instructed it to initiate the malicious routine on May 25, at midnight (local time).
On the same note, the ransom demand was just 0.1 bitcoins ($24 / €22), which is a very small price compared to what other threats of the same kind request.
Locker author deployed auto decryption
The decryption tool, dubbed Locker Unlocker, was created by Nathan Scott and was published on Bleeping Computer forum, along with complete usage instructions.
Even if the Locker infection has been removed, victims can still recover their data, as long as they know the bitcoin address that was assigned to them for paying the ransom.
Signing as “Poka BrightMinds,” the creator of Locker issued an apology on May 30, linking to the database with the decryption keys, and at the same time promising to trigger an automatic decryption routine on June 2, at midnight, for all impacted computers.
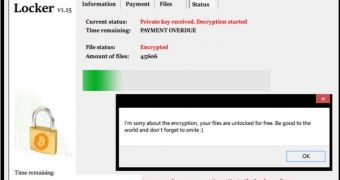
It appears that BrightMinds kept their word and sent the decryption command to all systems still infected by Locker, without asking for a dime in return. During the procedure, a message pops up apologizing for the trouble once more.
“I'm sorry about the encryption, your files are unlocked for free. Be good to the world and don't forget to smile :),” the note reads.
Only 22 bitcoin payments made
Some of the victims paid for their decryption key, earning the creator of Locker $169 / €152. According to information from Symantec, there were 22 payments between May 24 and May 31.
Most of the transactions are insignificant, while seven are larger, with a little more than $23 / €20 being transferred, suggesting that not many users actually paid the ransom.
The database dumped publicly contains a total of 62,703 entries with bitcoin addresses, each one being linked to a decryption key. The researchers checked all these addresses in order to determine the amount paid to the malware author.
 14 DAY TRIAL //
14 DAY TRIAL //