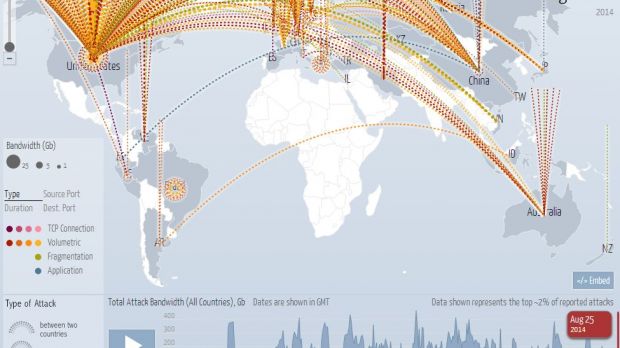
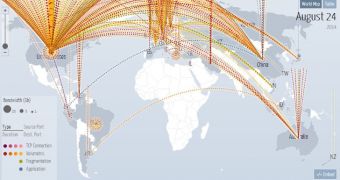
A group of hackers deployed a distributed denial-of-service (DDoS) attack on Sunday on Sony services, partially disrupting access to its networks for plenty of gamers.
John Smedley, President of Sony Online Entertainment (SOE), tweeted yesterday that Sony was under a massive DDoS attack, saying that games were impacted and that the bad traffic was being filtered with the help of Internet Service Providers (ISPs).
However, even with this mitigation, the problem persisted because the routes to reaching SOE services were also flooded.
The tweets he posted were related only to SOE, but PSN (PlayStation Network) was also experiencing trouble, with Sony acknowledging the disruption and informing that it was not because of the maintenance scheduled for Monday morning.
The attack was claimed by a hacker outfit going under the name of Lizard Squad (@LizardSquad), who said they were disgruntled by the way the company managed its money stream.
“Sony, yet another large company, but they aren't spending the waves of cash they obtain on their customers' PSN service. End the greed,” they said in a tweet.
During the DDoS, the hackers also tweeted a bomb scare to American Airlines, saying that the flight carrying John Smedley from Dallas to San Diego had explosives on board.
The airlines company has diverted the flight to Phoenix and the FBI is currently investigating the threat, as it is a matter of national security.
Smeadley had previously posted a message on the microblogging platform about making the trip, which allowed the hackers to look up the flight details.
Although DDoS attacks are not designed for stealing information from the server, but just to disrupt the provision of service, cybercriminals would sometimes use them as a smokescreen to penetrate the systems of the victim and exfiltrate information, as was the case with Gameover Zeus.
According to a blog post from Sony, no personal information had been accessed.
DDoS attacks targeting video game companies are not rare, but they are generally easy to deal with. However, sometimes hackers deploy organized, long-running attacks that can last for days.
Incapsula mitigated such an incident, which lasted from June 21 until July 28 and was directed at an undisclosed video game company. The perpetrators relied on significant resources, powerful enough to sustain a siege of 90+ Gbps of unamplified traffic.
An update on the matter tweeted a few hours ago by PlayStation Network says that the “service is currently returning for PS3 and PS Vita users, but you may experience slowness or login issues as the network stabilizes.”
In reference to the incident, Marc Gaffan, co-founder of Incapsula, said that “Our own research supports this, finding that DDoS attacks just like the one that recently hit the Playstation Network are up 240% in 2014. Attacks like this will continue to plague big name companies, thanks to the greater availability of resources for hackers.
“Persistent DDoS attacks can sometimes last for weeks and in a time when anyone can Google up a 'botnet for hire' and use it to execute a 20-40Gbps attack, from several thousands sources, organizations across the world need to re-evaluate their DDoS protection, or risk the consequences.”
Sony, yet another large company, but they aren't spending the waves of cash they obtain on their customers' PSN service. End the greed.
— Lizard Squad (@LizardSquad) August 24, 2014 [UPDATE]: Lizard Squad is not the perpetrator of the DDoS attack on Sony services; the attack has been claimed by @FamedGod, who provided proof of the hack.
 14 DAY TRIAL //
14 DAY TRIAL //