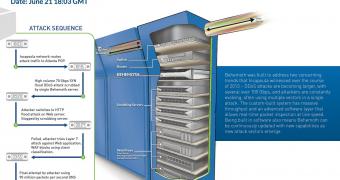
A massive DDoS attack directed at an undisclosed video game company due to an alleged business feud, lasted no less than 38 days and spewed over 50 petabits of malicious traffic at the target.
The perpetrators used extremely large DNS floods for the entire duration of the attack that started on June 21 and ended on July 28, channeling several tens of millions of requests per second, according to Incapsula, who mitigated the incident from start to end.
The company said in a blog post that the offenders “tried everything from massive network layer DDoS attacks to focused application layer (HTTP) floods, followed by dozens of SQLI and XSS attempts.”
On a regular basis, they relied on at least two of these attack vectors but they often ramped things up with five-vector attacks.
Incapsula says that the largest amount of packets was over 90 million per second, totaling a bombardment of more than 110 Gbps. Their DNS infrastructure was also hit with large SYN floods, in an attempt to disrupt the protection of the targeted service.
Suspicion of a business feud being at the root of the incident is supported by the fact that the attackers had sufficient firepower in their hands and were extremely determined in their activity.
“The ‘business feud’ theory is reinforced by the resources used during the attack. Looking at source IP data, Incapsula noticed the majority of malicious packets were originating from the same IP ranges. We knew that 20% of C-classes are typically responsible for ~80% of all DDoS traffic,” Incapsula says.
The resources leveraged in the incident were far from being consistent with an off-the-shelf botnet for hire capable of short-lived 20 Gbps blasts, which could be purchased on underground forums for a few hundred US dollars. An offensive lasting this long with capability to generate 90+ Gbps of unamplified DDoS traffic is clearly the work of professionals who DDoS for a living.
The long-lasting event was handled by Incapsula using a single “Behemoth” scrubbing server, which is capable of processing up to 170Gbps or 100Mpps worth of traffic.
The company under attack had contracted the DDoS mitigation services from Incapsula just a day before the incident started. At the time of the event Behemoth had spent a month being tested internally.
It goes without saying that Incapsula is mighty proud of their technology, especially after proving itself in an incident of this magnitude.
 14 DAY TRIAL //
14 DAY TRIAL //