At the beginning of 2013, security researchers from Vulnerability Lab identified a critical authentication bypass flaw in BillSafe, the German provider of payment upon invoice owned by eBay. The vulnerability was reported to PayPal, which addressed it earlier this month.
The vulnerability could have been leveraged by an attacker to bypass the session authentication and gain unauthorized access to PayPal and BillSafe accounts. The attacker could have easily changed the account’s passwords and associated email address to take over the customer profile.
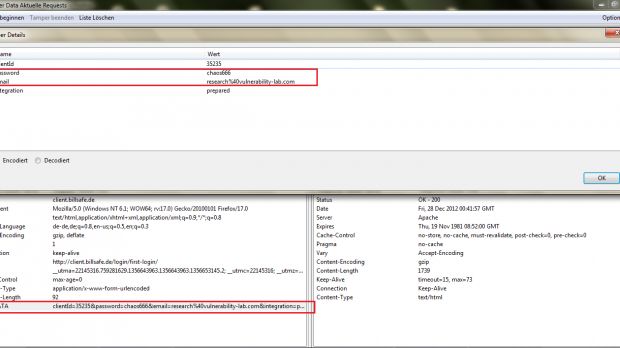
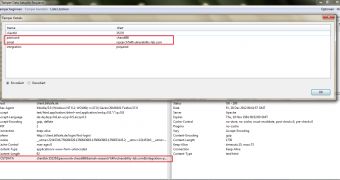
“The application is processing to request after account activation plain passwords without any kind of token protection mechanism. The vulnerability is located in the first login section of the BillSafe website when processing to load (after the activation) manipulated user/email/pass context,” Vulnerability Lab’s Benjamin Kunz Mejri told Softpedia.
“Remote attackers can manipulate accounts by live tampering the activation session link request. When the remote attacker is tampering the session live, the attacker only needs to exchange the plain requested values (name/ email/ pass) with the earlier valid requested values,” he added.
“After changing the vulnerable values the attacker only needs to send the same request again to reset any BillSafe client application account.”
The attack method identified by the experts doesn’t require any user interaction. The complete proof-of-concept code is available here.
This is not the first time when Vulnerability Lab experts identify security holes in PayPal services. They’ve been collaborating with the company for several months now, reporting issues such as SQL Injections, persistent cross-site-scripting, and other vulnerabilities that could have been leveraged to breach PayPal accounts.
Mejri says the vulnerability was patched within 90 days after the submission of an advisory report to PayPal’s website security team. The vulnerability disclosure has been coordinated by the PayPal website security team in cooperation with the developer team and a San Jose security manager.
 14 DAY TRIAL //
14 DAY TRIAL //