Researchers from Vulnerability Lab have identified a critical Blind SQL Injection vulnerability on the site of the world-renowned payment processor PayPal. The issue was reported to PayPal back in August 2012, but the company only addressed it earlier this month.
According to the advisory sent by Vulnerability Lab to Softpedia, the flaw could have been leveraged by a remote attacker, or a local user with low privileges, to inject their own SQL commands.
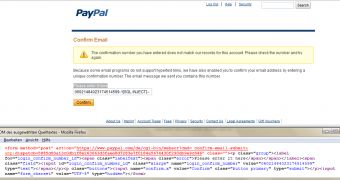
The security hole existed in the unique number field of the email confirmation module (see screenshot). The affected parameter was “login_confirm_number_id” bearing the name “login_confirm_number,”
“The validation of the confirm number input field is watching all the context since the first valid number matches. The attacker uses a valid number and includes the statement after it to let both pass through the PayPal application filter,” the advisory reads.
“The result is the successful execution of the SQL command when the module is processing to reload the page module. Exploitation of the vulnerability requires a low privileged application user account to access the website area and can be processed without user interaction.”
Cybercriminals could have exploited the vulnerability to compromise the web application or the affected module via a Blind SQL Injection attack.
It’s uncertain why it took PayPal so much time to fix the security hole, but according to the report timeline published by Vulnerability Lab, there’s a four-month period, between August and December 2012, in which the payment processor didn’t provide any feedback.
PayPal has rewarded the researchers with $3,000 (2,300 EUR) for identifying and responsibly disclosing the vulnerability.
For users interested in the technical part of this flaw, Vulnerability Lab has published a detailed proof-of-concept. The POC contains all the steps of the demonstration and it could be highly useful for security enthusiasts who want to learn more about such vulnerabilities.
 14 DAY TRIAL //
14 DAY TRIAL //