- Virus alerts
- By Catalin Cimpanu
- April 20th, 2016
Meet Panda Banker, One of the Most Recent Zeus Banking Trojan's Offspring
Panda Banker targets only banks in Australia, the UK
- Security Blog
- By Catalin Cimpanu
- April 18th, 2016

BitPay Bitcoin Processor Warns Against New Coinbitclip Trojan
Trojan spotted for the first time at the start of February
- Security
- By Catalin Cimpanu
- February 8th, 2016

Carbanak Trojan Returns, Now Targets Budgeting and Accounting Departments
Carbanak 2.0 detected, more dangerous than before
- Virus alerts
- By Catalin Cimpanu
- January 13th, 2016

SlemBunk Android Banking Trojan Continues to Wreak Havoc Around the World
SlemBunk continues to steal funds via Android devices
- Spyware Threats
- By Catalin Cimpanu
- January 10th, 2016

Spymel Info-Stealing Trojan Evades Antivirus Detection via Stolen Certificates
Zscaler researchers discover yet another malware family hiding with the help of stolen digital certificates
- Virus alerts
- By Catalin Cimpanu
- December 18th, 2015

SlemBunk Android Banking Trojan Targets 31 Banks Across the World
Trojan works by injecting fake logins into legitimate apps
- Security Blog
- By Catalin Cimpanu
- December 16th, 2015

TinyV Trojan Takes Aim at Jailbroken iOS Devices
Chinese iOS users under fire from TinyV trojan
- Security
- By Catalin Cimpanu
- December 7th, 2015

Malware Steals iOS and BlackBerry Backups via Infected PCs
BackStab technique helps criminals get their hands on your private data, via unprotected phone backups
- Virus alerts
- By Catalin Cimpanu
- December 5th, 2015

Hackers Build Rootnik Trojan on Top of Android Rooting Toolkit
Why create your own rooting functions when someone else has already put the effort into doing the same thing
- Virus alerts
- By Catalin Cimpanu
- December 3rd, 2015

Linux Users Targeted by New Rekoobe Trojan
First infections occurred around the start of October
- Virus alerts
- By Catalin Cimpanu
- November 23rd, 2015

Adware Uses Certificates & Windows UAC to Block Antivirus Installations
Vonteera adware is re-classified as a full trojan
- Security
- By Catalin Cimpanu
- November 11th, 2015

Thousands of Cheap Android Tablets Infected with Malware Sold on Amazon
All tablets were manufactured and sold by Chinese companies
- Virus alerts
- By Catalin Cimpanu
- November 11th, 2015
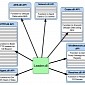
Kaspersky and Microsoft Security Products Abused to Install Spying Trojan
Bookworm trojan can be used to spy on infected victims
- Server related
- By Catalin Cimpanu
- October 28th, 2015

Malware Infects MySQL Servers, Enrolls Them in Worldwide DDoS Botnet
MySQL servers hijacked to carry out DDoS attacks
- Virus alerts
- By Catalin Cimpanu
- October 3rd, 2015

Linux-Targeting Malware Sets Up Proxies on Infected Machines
Duo of Linux trojans used to launch SSH brute-force attacks
- Virus alerts
- By Catalin Cimpanu
- October 2nd, 2015

Latest Upatre Trojan Version Targets Windows XP Users
XP is not dead, at least not for cyber-criminals
- Security
- By Catalin Cimpanu
- September 29th, 2015

XOR DDoS Botnet Uses Compromised Linux Machines to Launch 150+ Gbps Attacks
XOR DDoS botnet launches 150 Gbps attacks against Chinese targets