- Security Fixes and Improvements
- By Eduard Kovacs
- February 3rd, 2014

HP’s Zero Day Initiative Announces Pwn2Own 2014
A new challenge targeting Microsoft's EMET has been introduced this year
- Security Fixes and Improvements
- By Eduard Kovacs
- January 31st, 2014

GitHub Launches Bug Bounty Program with Rewards of up to $5,000 / €3,700
Check out the most important things you need to know about the bug bounty
- Virus alerts
- By Eduard Kovacs
- January 31st, 2014

Tor-Based Malware ChewBacca Used to Steal Card Data from POS Systems
Dozens of retailers from the US and other countries have been targeted
- Security Fixes and Improvements
- By Eduard Kovacs
- January 31st, 2014

Experts Find 28 Security Issues in Oracle’s Java Cloud Service
Researchers from Security Explorations have analyzed the platform
- Security Blog
- By Eduard Kovacs
- January 30th, 2014
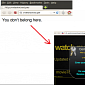
Scam Site Displays “You Don’t Belong Here” Message to Throw Off Suspicion
Blue Coat experts have come across the shady website
- Security
- By Eduard Kovacs
- January 29th, 2014

SpyEye Creator Wasn’t Too Good at Hiding His Tracks, Experts Say
He used weak passwords such as “loveme,” “kissme” and “Danny000″
- Virus alerts
- By Eduard Kovacs
- January 29th, 2014
Bitdefender and the Romanian Police Analyze Servers Used by Police Ransomware
267,000 computers infected over a period of five months
- Security Blog
- By Eduard Kovacs
- January 28th, 2014
Patnote Virus Used to Distribute ZeuS Trojan
Researchers from Trend Micro have analyzed the campaign
- Security Blog
- By Eduard Kovacs
- January 28th, 2014

Java Bot Can Launch DDOS Attacks from Windows, Mac and Linux Machines
Kaspersky researchers have analyzed the cross-platform malware
- Security Blog
- By Eduard Kovacs
- January 28th, 2014
Foursquare Flaw Could Have Been Exploited to Obtain Users’ Email Addresses
The issue was addressed by the social media company shortly after being reported
- Virus alerts
- By Eduard Kovacs
- January 28th, 2014

Researchers Discover First Android Bootkit, 350,000 Devices Already Infected
Rogue firmware is believed to be used to distribute the threat
- Spam Reports
- By Eduard Kovacs
- January 28th, 2014
NetSky Worm Spreads via Email Attachments
Different messages containing the threat are sent over and over to the same address
- Virus alerts
- By Eduard Kovacs
- January 28th, 2014
Israeli Government Organization Targeted by Palestinian Hacktivists
Seculert has been investigating an attack against Israel
- Security Blog
- By Eduard Kovacs
- January 27th, 2014

Bug That Can Be Exploited to Open Websites in Thunderbird Tabs Remains Unfixed
The issue was reported to Mozilla by an expert in November 2011
- Security Blog
- By Eduard Kovacs
- January 27th, 2014

Researcher Warns of Account Hijacking Flaws in “Connect with Facebook” Feature
The vulnerabilities will not be fixed any time soon
- Security Fixes and Improvements
- By Eduard Kovacs
- January 27th, 2014
Mozilla Fixes Thunderbird Flaw That Allowed Hackers to Insert Malicious Code into Emails
The issue was reported to Mozilla back in May 2013
- Security Blog
- By Eduard Kovacs
- January 27th, 2014

Expert Finds Remote Code Execution Vulnerability in Yahoo Server – Video
Yahoo hasn’t determined if the flaw falls within the the bug bounty program, so the Hegazy's efforts remain unrewarded