- Security
- By Eduard Kovacs
- April 1st, 2014

Experts Unhappy with Oracle’s Java Cloud Patching Process, Vulnerability Details Published
Security Explorations says Oracle is still working on vulnerability handling policies
- Security
- By Eduard Kovacs
- March 31st, 2014

FireEye Analyzes the 11 Zero-Day Vulnerabilities It Uncovered in 2013
The white paper published by the security firm is called "Less Than Zero"
- Hacking News
- By Eduard Kovacs
- March 31st, 2014

Hackers Can Unlock Tesla Cars by Stealing Owners’ Passwords
A security consultant has presented his findings at a recent conference in Singapore
- Virus alerts
- By Eduard Kovacs
- March 31st, 2014

Pre-Installation Service Used to Install Malware on Android Phones in China
The service in question is used to install apps on over 1 million devices each month
- Security Blog
- By Eduard Kovacs
- March 28th, 2014

Google Experts: 21 of Top 25 News Organizations Targeted by State-Sponsored Hackers Reuters
The researchers have presented their findings at Black Hat in Singapore
- Security
- By Eduard Kovacs
- March 28th, 2014

Cybercriminals Hijack WordPress Websites with Free Premium Plugins
Sucuri experts have identified a number of websites that offer such plugins
- Security
- By Eduard Kovacs
- March 21st, 2014
Unpatched PHP Installations Enable Cybercriminals to Exploit Old Vulnerability
The PHP flaw was found back in May 2012 and it was patched shortly after
- Security Blog
- By Eduard Kovacs
- March 20th, 2014

BlackOS: New Malicious Software Used by Cybercriminals to Redirect Traffic
A new cybercrime package from the creators of "Tale of the North"
- Security
- By Eduard Kovacs
- March 20th, 2014

Alleged Operator of SSNDOB Identity Theft Service Identified
Experts believe he's a 24-year-old from the disputed territory of Abkhazia
- Virus alerts
- By Eduard Kovacs
- March 20th, 2014
New ZeuS Generates Income for Its Masters by Displaying Sites on Infected Computers
Another variant is designed to steal Bitcoin wallets
- Security Blog
- By Eduard Kovacs
- March 19th, 2014

Expert Finds RCE Flaw in Yahoo After Logging in with “Admin/Admin” Credentials
Behrouz Sadeghipour is the security researcher who uncovered the vulnerability
- Security Blog
- By Eduard Kovacs
- March 19th, 2014

Security Researcher Accidentally Crashes Google Play When Testing POC App
This is the second time this Turkish expert is involved in such a story
- Server related
- By Eduard Kovacs
- March 18th, 2014
ESET Uncovers Server Botnet That Infected over 25,000 UNIX Machines
Researchers say this is the largest server botnet they’ve seen so far
- Security Blog
- By Eduard Kovacs
- March 14th, 2014
Cybercriminals Leverage Mass Stabbing in China to Distribute Gh0st RAT
A backdoor is hidden inside a harmless-looking document file
- Security
- By Eduard Kovacs
- March 14th, 2014
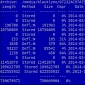
Hackers Who Hijacked Mt. Gox CEO’s Blog Tricked People into Installing Bitcoin Stealer
Kaspersky experts have analyzed the files “leaked” by the hackers
- Security
- By Eduard Kovacs
- March 14th, 2014

Researchers Rewarded with a Total of $850,000 / €613,000 at Pwn2Own 2014
Google Chrome has been hacked on the second day of the competition
- Virus alerts
- By Eduard Kovacs
- March 13th, 2014
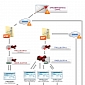
FireEye Finds Connection Between “Siesta” and Notorious Chinese Espionage Unit
Is APT1 behind the recently uncovered Siesta espionage campaign?