Two vulnerabilities exist in BMW's ConnectedDrive Web portal that can allow an attacker to manipulate car settings related to its infotainment system.
ConnectedDrive is the name of BMW's in-car infotainment system. The system can be used as it is, in the car, or via a series of connected mobile apps that allow the driver to manage vehicle settings through their mobile devices. Besides the mobile apps, this service also has a counterpart for the Web.
Benjamin Kunz Mejri, security researcher for Vulnerability Lab, published yesterday two zero-day vulnerabilities in the ConnectedDrive portal that BMW has failed to patch for the past five months.
Issue #1: VIN session hijacking
The first issue is a session vulnerability that allows a user to get access to another person's VIN - Vehicle Identification Number.
VINs are car IDs attached to each user's account. A VIN code is used to back up a car's ConnectedDrive settings to their account. Changing these settings in the Web portal will also change them on the car and attached apps.
Mejri says that his attack allowed him to bypass VIN session validation and use another VIN to access and then edit another user's car settings.
Some of the settings available through the ConnectedDrive portal include the ability to lock/unlock the vehicle, manage song playlists, access email accounts, manage routes, get real-time traffic information, and so on.
Issue #2: XSS on the ConnectedDrive portal
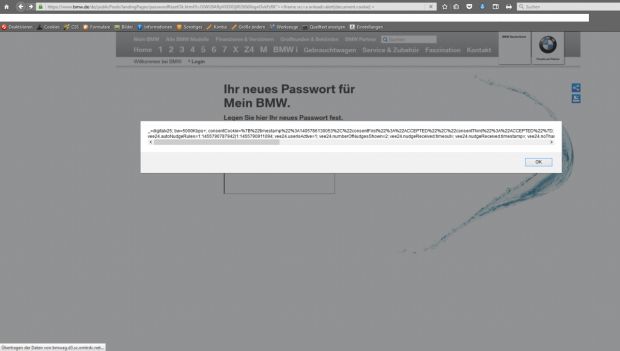
The second issue is an XSS (cross-site scripting) bug on the portal's password reset page.
This XSS bug can lead to any of the regular complications that come from such Web attacks, such as browser cookie harvesting, subsequent CSRF attacks, phishing attacks, and more.
Mejri claims he notified BMW of these two issues in February 2016. Since BMW has failed to answer Mejri's bug reports in time, the researcher went public with his findings. An in-depth description of the issues, complete with proof of concept exploit code can be found here (first issue) and here (second issue).
Almost a year ago, security researcher Samy Kamkar revealed that his OwnStar car hacking toolkit also worked with BMW's Remote service.

 14 DAY TRIAL //
14 DAY TRIAL //