Security researchers from Guardicore revealed a sophisticated malware attack that managed to compromise some 800 devices belonging to a medium-sized company in the medical tech industry.
In a technical analysis of the attack, Guardicore explains that the malware infection was disguised as a WAV file and included a Monero cryptominer, using the notorious EternalBlue vulnerability to compromise other devices in the network.
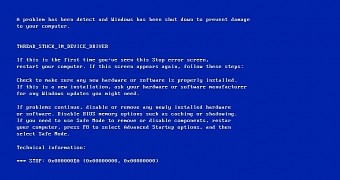
The only thing the malicious actors got wrong was code that eventually caused a Blue Screen of Death (BSOD) on the infected machine, eventually raising suspicion and triggering an in-depth investigation into the fatal crash.
The BSODs were first experienced on October 14, Guardicore says, when its researchers discovered that machines hitting the fatal crash were trying to execute a long command line that was, in fact, a base-64 encoded PowerShell script.
Monero miner
After decoding the script, researchers obtained a readable Powershell script that was used to deploy the malware.
“We obtained a readable Powershell script which starts by checking the system architecture (based on pointer size). Then, it reads the value stored in the registry subkey mentioned above and loads the value into memory using the Windows API function WriteProcessMemory. The code – namely, the malware payload – is executed by obtaining and invoking a function pointer delegate,” the researchers note.
A total of 800 devices in the network, which represents nearly 50 percent of the device fleet, were infected.
The malware attempted to spread to other devices in the network using an exploit based on EternalBlue, the same vulnerability that was used by WannaCry back in 2017 to infect thousands of computers across the world.
After a reverse engineering of the malware, the researchers discovered that it was actually hiding a cryptominer disguised as a WAV file.
“The malware contains a cryptomining module based on the open-source XMRig CPU miner. It uses the CryptonightR algorithm to mine Monero – a popular privacy coin. In addition, the malware makes use of steganography and hides its malicious modules inside clean-looking WAV files,” Guardicore explains.
The full removal of the malware, including terminating the malicious processes, prevented the BSODs from taking place on the previously-compromised devices.
 14 DAY TRIAL //
14 DAY TRIAL //