On September 5th, Independent security researcher Bob Diachenko found a public customer record database owned by Veeam, data recovery and backup company who forgot to secure its data.
Veeam, which markets itself as "global leader in Intelligent Data Management," seems to have misplaced its login credentials for the massive 200 GB database of customer records as it could have been accessed by anyone who knew where to look.
After its findings, Diachenko notified the company but failed to get in touch with Veeam, although after subsequent attempts of contacting them, the company did manage to secure the database on September 9h.
According to Diachenko, Shodan's search engine for Internet-connected devices indexed the database' Amazon-hosted IP on August 31st, which means that said database was open to access at least for nine days.
The leaked 200 GB database bundled around 445 million records
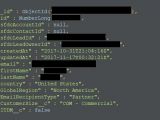
As disclosed in Diachenko's blog post, Veeam's database contained in excess of 445 million records related to an automated marketing campaign using Marketo, and it included information such as customer e-mail addresses, full name, IP address, and organization size, among many other entries.
Although the data leak did not contain sensitive data such as plain text or hashed passwords, the database can still prove to be a treasure trove for any threat actors who managed to get access to it until Veeam managed to secure it and who could use it for both phishing and spam-based attacks.
"It is also a big luck that database was not hit by a new wave of ransomware attacks which have been specifically targeting MongoDBs (with much more extortion amount demand than it was last year)," said Diachenko in his write-up.
All database administrators are advised to take into account that MongoDB released security guidelines for their database product a year ago, at the same time adding new inbuilt security features such as encryption, access controls, and detailed auditing.

 14 DAY TRIAL //
14 DAY TRIAL //