The personal email accounts of U.S. Treasury officials were targeted by a spearphishing attack campaign started during early October 2018 and orchestrated by the Iranian Charming Kitten cyberespionage group.
Security company Certfa, which analyzed the phishing operation, dubbed it "The Return of The Charming Kitten" to mark the return of the threat group.
According to Certfa, "the hackers - knowing that their victims use two-step verification - target verification codes and also their email accounts such as Yahoo! and Gmail. As a result, Certfa believes the safest existing way to confront these attacks is using Security Keys such as YubiKey."
Certfa's analysis discovered that the phishing campaign which targeted US financial officials and was discovered in October 2018 is a direct result of the sanctions imposed by the USA against the state of Iran.
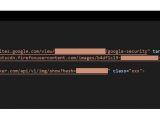
Moreover, the Iranian government sponsored group behind this operation was linked to the accounts-support[.]services domain and is believed to also be connected to the Islamic Revolutionary Guard Corps (IRGC).
One month later, the Charming Kitten threat group switched objectives, this time going after "civil and human rights activists, political figures and also Iranian and Western journalists."
During its phishing campaigns, Charming Kitten used both unknown messaging and email accounts, as well as previously hacked into accounts of public figures that made it easier to persuade their prospective victims to install malicious payloads on their systems.
Charming Kitten chose to only monitor compromised emails to stay undetected
Furthermore, the Iranian threat actors used spear-phishing research techniques, collecting extensive information regarding their targets and tailoring the tools and methods to be used during the attacks beforehand depending on each victim's profile.
Also, unlike previous campaigns ran by Charming Kitten, during this one the bad actors would leave the compromised email accounts untouched, not changing passwords and only monitoring communications to remain undetected as long as possible.
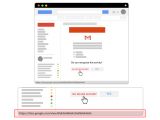
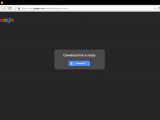
Among the methods used to trick targets into downloading and installing malware on their computers, the hackers used fake Google Drive file sharing pages and malicious email alerts of unauthorized access into their Gmail accounts.
Despite the group's usage of "Virtual Private Networks (VPNs) and proxies with Dutch and French IP addresses to hide their original location," Certfa still managed to detect their real IP addresses used during the development phase of the "The Return of The Charming Kitten" campaign.

 14 DAY TRIAL //
14 DAY TRIAL //