Forcepoint's security researchers found traces of a threat group which targets energy and automotive companies using CAD malware via a campaign running since at least 2014.
CAD malware uses maliciously crafted design files which auto-load encrypted scripts designed as run-of-the-mill malware downloaders that drop a wide variety of malicious tools on the infiltrated system.
However, unlike in the case of phishing attacks which use malicious documents attached to email messages, CAD malware campaigns will host the malicious project files either on a private hosting server or a public file sharing service, serving the target with a direct download link.
There are also campaigns which use USB storage drives or CDs/DVDs sent via postal services, exploiting the fact that a lot of enterprises would instead receive this type of documents in physical form rather than downloading them from the web, from a potentially not trustworthy source.
The latest victims compromised by the bad actors behind the CAD malware campaign observed by the ForcePoint researchers were infected using AutoCAD project files that automatically loaded AutoLISP-based scripts upon opening.
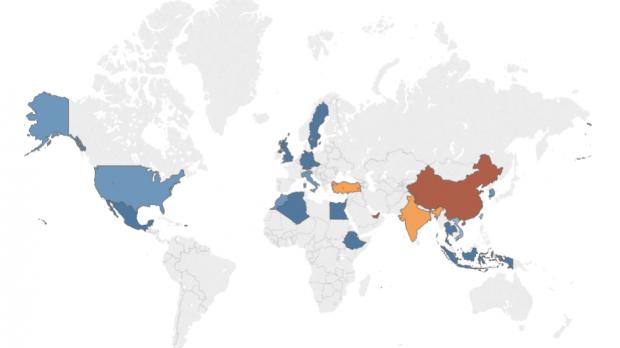
"Our telemetry shows the infection extant at least as long ago as late 2014 and, further, that new victims appear to have been infected as recently as mid-2018 with the majority of infected machines appearing in China, India, Turkey, and the UAE," says ForcePoint.
AutoCAD users can enable security control to protect themselves from CAD malware
By analyzing the C2 domain pivoting process, the researchers noticed that the adversaries successfully attacked companies from the energy sector with some renewable energy industry organizations having been compromised.
The AutoCAD malware campaign also targeted entities related to the automotive industry with a possible cyber-espionage focus, as well as other firms connected to constructions and even government-run road maintenance authorities.
According to ForcePoint, AutoCAD users can protect themselves from CAD malware campaigns targeting them by enabling the security variables which control what the AutoCAD software loads automatically.
Additionally, AutoCAD users can also enable a warning that will be displayed when CAD design documents load scripts in the background.
 14 DAY TRIAL //
14 DAY TRIAL //