Thousands of compromised websites running the WordPress Content Management System (CMS) are redirecting their users to tech support scam pages, as reported by Malwarebytes Labs' Jérôme Segura.
Not surprisingly, given the amount of website hacking incidents involving content managing systems such as Joomla, Drupal, and WordPress, Malwarebytes Labs detected a new wave of hacked sites, all running the WordPress CMS.
Even though the attack vector used to infiltrate the websites is still unknown, the researchers know that the bad actors use multiple ways of injecting malicious code with the goal of sending visitors to browser lock attack sites.
As Segura details, the attackers can add an encoded blurb of code within the hacked website's HTML headers tag, a JavaScript-based one line script which loads the full attack script or malicious code within the WordPress database's wp_posts table.
The number of affected Wordpress websites is growing every day
The security researcher also discovered the number of Wordpress websites "enrolled" in this tech scam campaign is increasing every day, a sure sign of the crooks trying to expand the scope of the attack to even more targets.
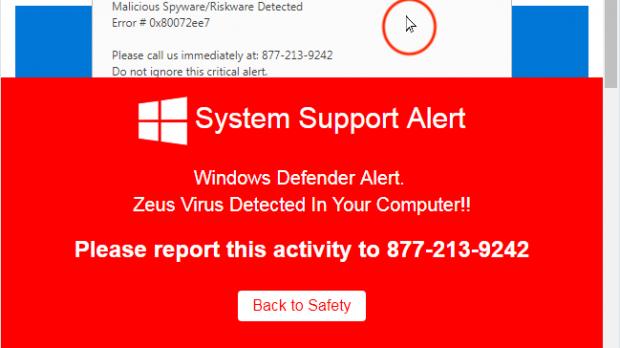
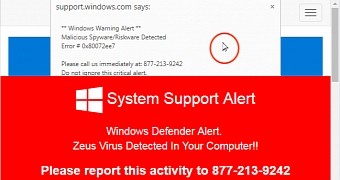
Some of the tech support scam websites have been found to use the browser lock vulnerability Malwarebytes has found a week ago and which is still waiting for a patch.
According to Malwarebytes Labs' previous advisory, this new type of browlocker page affects the latest Google Chrome version, and it operates by hijacking the user's mouse by substituting it with an offset mouse pointer and stopping him from closing the page.
The researchers do not specify any exact steps to mitigate this type of cyber assault because of the multiple possible attack vectors and ways the WordPress websites are used to send their users to malicious sites.
However, website owners should make sure that their WordPress installation and all the plugin they use are up to date, as well as cleaning all their sites' pages of any out of place code, pages, backdoors or unknown files.
 14 DAY TRIAL //
14 DAY TRIAL //