Omniscient, the administrator of Hack Forums, the Internet's biggest freely accessible hacking-related forum, announced on Friday, October 26, that he would remove the DDoS-for-Hire section from the forum.
His decision came after a series of events that have tied his forum to DDoS attacks carried with the Mirai botnet.
It all started when a Hack Forums user named Anna-Senpai released the source code of the Mirai malware via the forum, which drew a massive and immediate attention from security researchers.
A person who had taken Mirai's source code and modified it, had then used it to launch a DDoS attack on the network of Dyn, a managed DNS service, which resulted in a large section of the Internet becoming unavailable.
Flashpoint report puts law enforcement focus on Hack Forums
Following this incident, security firm Flashpoint published a report suggesting that Hack Forums members might be behind the attack.
Three days before making this decision, the forum's administrator had shown interest in shutting down the section, following a bad encounter with US media.
“ There is a reason I separated it, made it Ub3r only, and disallowed profile advertising. I can absolutely see a day when it's removed entirely. Could be very soon too. ”
Omniscient feared that his forum was being demonized and made a scapegoat for the Dyn DDoS attack and the current state of freely-accessibly DDoS-for-Hire services.To be fair, Hack Forums is not the only forum where these types of services are advertised, but it has the biggest visibility.
Omniscient was also mad that a quote he provided to the Washington Post had been ignored and only certain portions used, giving the forum a bad image. The full statement the admin provided is available below.
“ Hackforums is a website mainly devoted to like-minded individuals who believe in learning new technical computer skills including security aspects. Unfortunately not all members of HF use their knowledge for good. HF has very strict rules forbidding a variety of topics but at the same time we recognize that some topic discussion has to remain that could be used in a harmful manner. Similar to a gun store owner knowing that a weapon he sells might potentially be used for a murder. We do our best to allow members a voice and knowledge that they may not be allowed to have in their own country or at other websites. Our member base includes many who are in our own government security, tech industry, security technicians, military, and even law enforcement. We've been online almost ten years and we have many success stories from members who went on to earn college degrees, accreditations and certifications in computing, networking, or security. Members have found jobs in the tech industry and often contact us with gratitude for being their first entry into the world of true computing and not just using a web browser, apps, and social media. While we'd like to see a higher moral standard from members we also can't force ethics onto people simply with policy. Members are going to do what they do no matter where or who they learned it from. If a news agency reports about a new drug in the streets and a teenager seeks it out does that make the reporter responsible? We do our best to remain neutral the same way that Twitter, Reddit, or Youtube tries not to get involved in member content and censorship. ”
Speaking to the Hack Forums community, he also added:“ I can't be sure what the WP article is going to say but I can't imagine this attention is going to be a good thing. Already a Senator is calling for a hearing on the Internet of Things. In the end there could even be new laws which effect [sic] us all. So for those responsible for the attacks and creating this mess....you dun goofed. I expect a lot of backlash to come out of this. This does not make me happy at all. ”
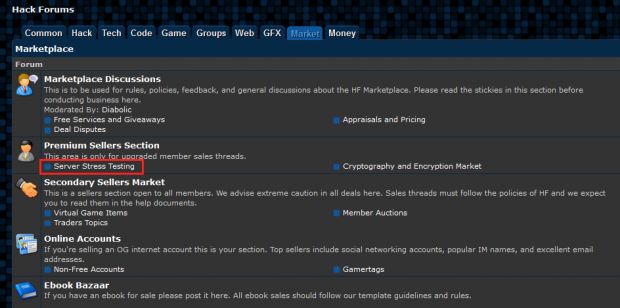
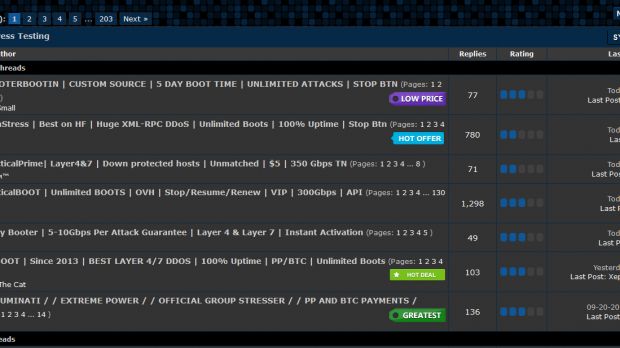
Fearing that law enforcement might soon be breathing down his neck, seize its servers, and arrest administrators, like they did with Darkode, Omniscient decided to remove the Server Stress Test (SST) section from his site on his own."Server stressing" is the name often given to "DDoS-for-Hire" services, in an attempt to legitimize their existence. Omniscient's full SST shutdown announcement is below.
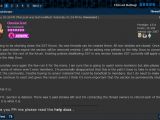
“ I'm going to be shutting down the SST forum. No new threads can be created there. All non-stickies are closed. Once the current paid stickies expire the section will be removed entirely. I will be adding new policies to the Help Docs to concerning SST topics for the rest of the forum. Existing policies disallowing SST in any section besides SST currently still apply until I update the Help Docs. Unfortunately once again the few ruin it for the many. I am sure this is going to upset some members but also please many, some of whom aren't even members. I'm personally disappointed that this is the path I have to take in order to protect the community. I loathe having to censor material that could be beneficial to members. But I do need to make sure that we continue to exist and given the recent events I think it's more important that the section be permanently shut down. ”
A few hours later, he decided to stop drawing it out and delete the section outright.“ F'it. Section is deleted. There was 5 paid stickies left and I'm contacting the thread owners to refund each of them. Again, it is what it is. ”
At the time of writing, the SST section has been removed from the forum, and accessing its direct URL yields a "No forum exists" error.
What Omniscient fails to realize is that his forum is also advertising or selling other questionable "testing" tools such as RATs, keyloggers, and hacking tutorials.
A theory about the Dyn DDoS attacks
Editor's note & Food for thought: While researching this story, we came across an interesting opinion from one of the more respected Hack Forums members who claimed that the people who attacked Dyn never intended to attack it in the first place.
The user, who sells the Qbot malware and goes by the name of qbotwithasupermicroontop, said the attackers only tried to DDoS the Play Station Network on the day EA launched the Battlefield 1 game, which was October 21, the day of the Dyn DDoS attack. He writes:
“ this is funny, only because they didnt actually attk DYN fun fact DYN was never intentionally attkd until later that day PSN was the target (bf1 release) they used DYN's ns: ns00.playstation.net, ns01.playstation.net, ns02.playstation.net etc. ”
Hackforums removing the DDoS service section is a huge milestone, the culture brought about by it has been breeding scriptkiddies for years. — MalwareTech (@MalwareTechBlog) October 29, 2016
@MalwareTechBlog Everyone starts somewhere but when booter services are an entire industry, people never grow up and move on. — MalwareTech (@MalwareTechBlog) October 29, 2016
@SebWinfieId @MalwareTechBlog Yep. Removed yesterday... I think... pic.twitter.com/Bus25UrnUL — Catalin Cimpanu (@campuscodi) October 29, 2016
 14 DAY TRIAL //
14 DAY TRIAL //