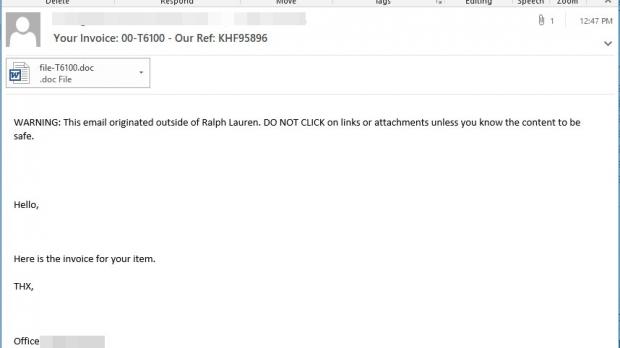
An increase in spam e-mails spreading Word documents containing scripts downloading the self-propagating Emotet banking Trojan has been observed during the past week according to an analysis by Malwarebytes Labs' Director, Adam Kujawa.
The Emotet malware is a well known malicious program among security researchers, a tool used by attackers to infect computers via spam e-mails to steal financial info such as bank logins or cryptocurrency wallets.
Furthermore, Emotet can exfiltrate proprietary info and data, login credentials, and Personally Identifiable Information (PII), the leading cause behind identity theft incidents.
Emotet is also known to act as a transport conduit for other banking Trojans or, in the case of the current campaign, for Trickbot, an information-stealing and highly-customizable modular botnet agent malware using compromised routers and IP cameras as command-and-control (C&C) servers.
For propagation across the network, the Trickbot malware uses a verified method the EternalBlue SMB exploit developed by the U.S. National Security Agency (NSA) and leaked by the Shadow Brokers hacker group in April 2017.
300K spam e-mails spreading the Emotet banking Trojan blocked every three hours by Windows Defender
According to Microsoft's Windows Defender Twitter account, at the peak of the spam campaign, Windows Defender was blocking around 300,000 e-mails with Word document attachments containing TrojanDownloader:O97M/Powdow.OB infected scripts every three hours.
After the victims would enable the macro feature in their Microsoft Office installation and run the macro scripts contained within the malicious attachment, the Trojan-Downloader script would download the Emotet banking Trojan payload and compromise the target's computer.
Once the victim's machine has been compromised, Emotet will start collecting data according to instructions contained within the malware modules it comes with.
Emotet also propagates itself throughout the network using either the EternalBlue vulnerability made famous by the WannaCry ransomware (just like Trickbot) or the inbuilt spam module using the infected computer and the user's address book as spreading devices.
We're seeing a large #Emotet spam campaign with maldocs, originally spewing malicious Word documents, but now sending out PDFs. At its peak, we blocked over 300k spam emails in 3 hrs. Detection name: TrojanDownloader:PDF/Domepidief.A https://t.co/pWja45EInR pic.twitter.com/8uAdQ6d7v3 — Windows Defender Security Intelligence (@WDSecurity) September 18, 2018
 14 DAY TRIAL //
14 DAY TRIAL //