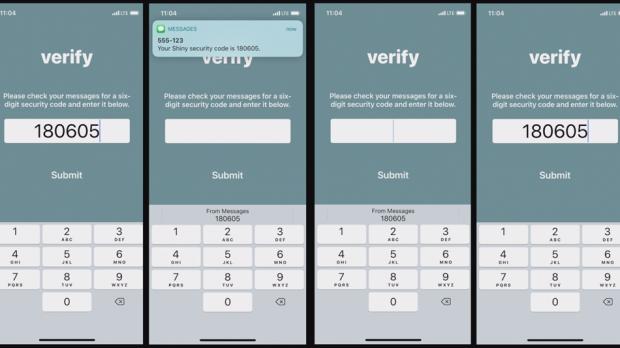
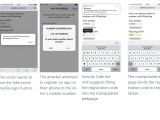
Security expert Andreas Gutmann warned in July that the Security Code AutoFill feature added in iOS 12 could allow potential cybercriminals to perform man-in-the-middle attacks to defraud users and siphon funds out of their accounts.
Although Apple patched the Security Code AutoFill feature which automatically displays one-time passcodes received by SMS as AutoFill suggestions, the mechanism allowing bad actors to exploit the feature is still there.
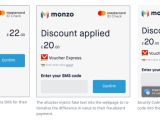
Moreover, Cupertino redesigned Security Code AutoFill to scan the SMS to the amount of money exchanged in the transaction that needs to be verified and, if it finds it, it will display the one-time code as an autofill option to help users make sure that the value of the transaction has not been modified by a malicious third party.
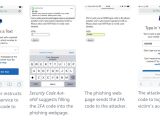
As detailed by Gutmann in his analysis, "However, Security Code AutoFill doesn’t display all the information necessary for users to make an informed decision on whether to submit the security code. Yet, it relies on the user to make the right decision. It is, for example, important to know which service sent the security code and for what reason. "
This means that bad actors could potentially tamper with other values included in the incoming SMS such as the destination of the banking transaction the user has to verify, increasing the risk of banking fraud exponentially.
Although patched by Apple, the Security Code AutoFill feature still exposes iOS and macOS users to attacks
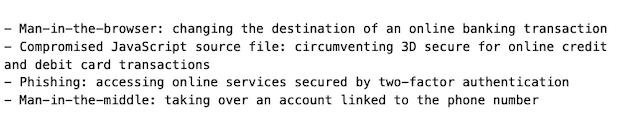
Gutmann describes four types of attack vectors that can be used to compromise transactions verified using one-time passcodes sent via SMS, namely man-in-the-browser, compromised JavaScript source file, phishing, and man-in-the-middle.
"Each attack is described as an attack on a different type of online service: online banking, credit card payment, online account, and app registered to a phone number," according to Gutmann.
Furthermore, although it might seem otherwise, all these attacks exploit the default behavior of the Security Code AutoFill feature and not other bug or programming mistakes.
Even though Apple's fix of the initially reported issue in the Security Code AutoFill feature does help, iOS 12 and macOS Mojave users are still vulnerable to multiple types of attacks that could expose them to bank fraud.
Unfortunately, users are not able to mitigate this issue in any way besides giving up on the Security Code AutoFill feature and returning to manually entering the one-time passcodes they receive via SMS.
 14 DAY TRIAL //
14 DAY TRIAL //