Malwarebytes Labs Jérôme Segura details in a new report the behavior of a new malvertising campaign named Partnerstroka which uses a browser locker technique specifically designed for Google Chrome as well as adaptive algorithms to cover most browsers and platforms.
Tech support scams are still a prime threat for most Internet users and can use multiple ways of luring their victims, from telephone calls impersonating Microsoft staff to malicious tech support ads and pop-ups designed to redirect targets to payment pages.
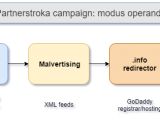
Among all types of threat actors observed using malvertising methods to scam their victims, Partnerstroka is a new tech support scam group which uses old and verified techniques but with a twist: they use a new type of browser locking method specifically designed for Google Chrome.
More precisely, as Malwarebytes Labs found out during their research, this new browlocker affects the latest Google Chrome 69.0.3497.81 version, and it works by hijacking the user's mouse by replacing it with an offset mouse pointer and preventing him from closing the page.
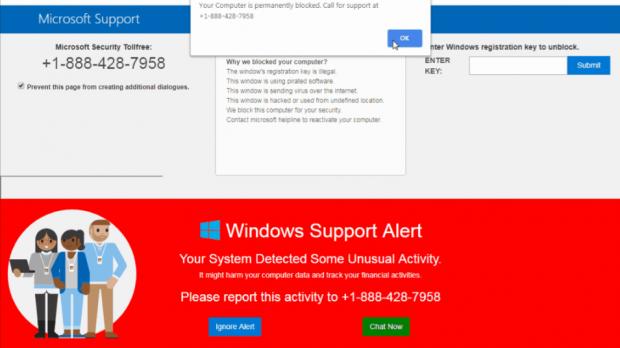
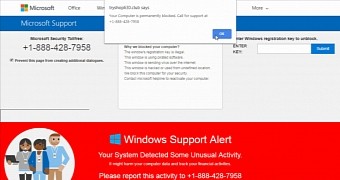
Next, Partnerstroka's browser locker landing page, which poses as an official Microsoft Support page, displays a pop-up asking the unsuspecting victim to call for support using a "+1-888" telephone number.
Browser lock pages are specifically designed to hijack the mouse pointer in Google Chrome
The security research team has reported the browser lock method via the Chromium bug tracker portal and got a quick reply with an image of the offset pointer.
The Google Chrome browser lock method used by the Partnerstroka scam group works on all major operating systems (i.e., macOS, Windows, Linux, and ChromeOS) and there is no mitigation solution to avoid having your browser locked if you happen to encounter on their malicious landing pages.
"Due to the size and ever-changing nature of the infrastructure between different browser locker campaigns, applying a domain/IP database approach against them is not an effective solution," said Jérôme Segura. "Although it does offer some coverage, scammers are always a step ahead because of their ability to register new (yet to be detected) domain names."
The only thing you can do at the moment is to make sure that you update your Google Chrome browser as soon as a new version containing a fix for this specific vulnerability is released.
 14 DAY TRIAL //
14 DAY TRIAL //