Security researchers from US firm Sucuri are warning WordPress site owners against installing pirated themes and plugins, especially from the GoMafia.com website.
The company's engineers report that, during their most recent site cleaning operations, one of them discovered some encoded code in the footer of one of their client's sites, loaded via a premium WordPress plugin.
JavaScript file secretly loading black hat SEO spam
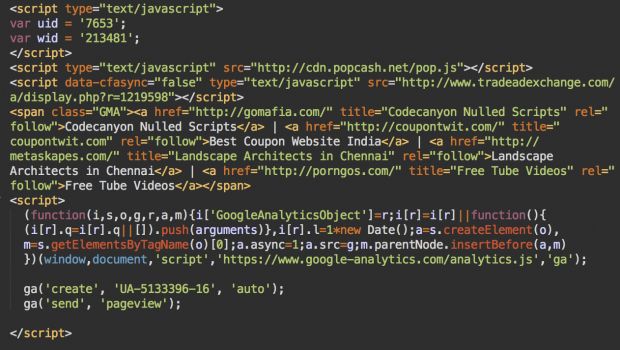
Unscrambling the data, this line of encoded PHP was loading a JavaScript file from the GoMafia server. A close look at this file revealed that the crooks behind this campaign were embedding several items on the victim's site, behind their back.
The crooks were first inserting four HTML links to four different websites. CSS code was hiding these links from the human eye, but not from search engines. The obvious goal of this tactic was to add these links to all sites on which the plugin was being loaded, in an attempt to boost search engine ratings for the four sites.
One of these links was GoMafia.com while the other three were all links to websites that Sucuri engineers say were registered by the same person, an Indian developer from Tamil Nadu, named Sathish Kumar, working for a Web development company called Kenzest(.com).
Sucuri also discovered that these four websites were running on the same server, also shared by Kenzest.
Crooks were also loading unwanted, malicious ads
Furthermore, the malicious footer script would also load a Google analytics code, which the previous four websites also shared among them.
Last but not least, the same footer code would also embed ads on the infected site. These ads brought revenue to the crooks, were very intrusive, sometimes badgering the user, and even linking to questionable if not pure dangerous products.
Taking a look at the source of all this malicious code from the GoMafia.com website, Sucuri understood how all this was possible. GoMafia is a portal that proclaims to provide access to nulled (pirated) WordPress themes and plugins, from WordPress marketplaces such as CodeCanyon and ThemeForest.
Webmasters should avoid using nulled scripts
It was pretty easy to reach the conclusion that Kumar had created GoMafia to distribute nulled WordPress plugins and themes that contained his malicious code.
Users downloading content from GoMafia would end up with malvertising and hidden black hat SEO on their sites.
Kumar didn't distribute a backdoor with his nulled plugins, unlike another Indian developer caught doing something similar. Nevertheless, by changing a few lines of code in the dynamically loaded JavaScript file inserted in the infected site's footers, he could have easily pushed anything he wanted to those sites.
Seeing that Kenzest was offering SEO services on its website, Kumar was probably in the process of building his black hat SEO emporium, before replacing the links to his own websites (for nulled software, interior design, coupons and adult material) with anything his clients wanted to boost in search rankings.

 14 DAY TRIAL //
14 DAY TRIAL //