New versions of the nginx web server have been released on November 6 to patch multiple security issues affecting versions before 1.15.6, 1.14.1 and allowing potential attackers to trigger a denial-of-service (DoS) state and to access to potentially sensitive info.
According to its project website, nginx is an open source "HTTP and reverse proxy server, a mail proxy server, and a generic TCP/UDP proxy server" released under the 2-clause BSD-like license.
Furthermore, "According to Netcraft, nginx served or proxied 25.28% busiest sites in October 2018. Here are some of the success stories: Dropbox, Netflix, Wordpress.com, FastMail.FM" (emphasis ours.)
"Two security issues were identified in nginx HTTP/2 implementation, which might cause excessive memory consumption (CVE-2018-16843) and CPU usage (CVE-2018-16844)," as detailed in nginx's advisory.
Moreover, "The issues affect nginx compiled with the ngx_http_v2_module (not compiled by default) if the "http2" option of the "listen" directive is used in a configuration file."
To exploit the two issues described above, attackers can send specially crafted HTTP/2 requests which will lead to excessive CPU usage and memory usage, eventually triggering a DoS state.
All servers running unpatched nginx versions are vulnerable to DoS attacks
The third security issue (CVE-2018-16845) affects the MP4 module, allowing attackers to either cause an infinite loop, a crash, or a memory disclosure state in the worker process with the help of a maliciously crafted MP4 file.
This last security problem only affects servers which run nginx versions built using the ngx_http_mp4_module and with the mp4 option enabled in the config file. Additionally, the issue will only affect a server if the attackers also manage to trigger the processing of the malicious MP4 file.
While the HTTP/2 vulnerability affects all nginx versions between 1.9.5 and 1.15.5, the MP4 module security issue affects servers running nginx 1.0.7 and upward, as well as nginx 1.1.3 or higher.
To mitigate the two issues server admins have to update their nginx installation to the 1.14.1 stable or the 1.15.6 mainline versions.
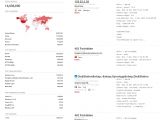
At the moment, a quick Shodan search revealed more than 14 million servers running unpatched nginx versions (14,036,690 to be more exact), while only 6992 servers are patched.

 14 DAY TRIAL //
14 DAY TRIAL //