Microsoft, along with Google, Apple, and Yahoo, plays an important role in the lives of online users, being one of the four major identity providers that basically cover the entire online userspace.
Through its Microsoft Account and Microsoft Azure Active Directory services, the company is helping regular and corporate users alike by providing them with a central identity.
The Microsoft identity empire
Microsoft Account, formerly known as Windows Live ID, is a username and password-based identity, which regular Internet users employ to sign into services such as Bing, Outlook.com, OneDrive, Windows Phone, Skype, Xbox LIVE, Windows 8.1, Windows 10, and many others.
Depending on each user's personal setup, a Microsoft Account identity, if compromised, can allow attackers access to a wide range of personal data, ranging from devices to photos, and from contact lists to sensitive documents.
Microsoft's second service for managing user identities is called Azure Active Directory (AAD) and is a commercial service offered to corporate entities. This service is a single sign-on system that grants users access to thousands of cloud (SaaS) apps such as Office 365, Workday, Box, Google Apps and more.
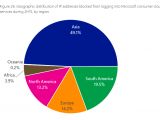
Microsoft is boasting that 90 percent of the world's 2,000 largest organizations use Azure Active Directory to manage user access to their cloud services. The company says it has 8.24 million AAD tenants, which in turn manage identities for 550 million users.
Microsoft says that 10M of the daily 13B login attempts are attacks
According to a Microsoft security report, the company is seeing over 13 billion authentications per day for these two services (1.3 billion for AAD), of which, the company says over 10 million (per day) are cyber-attacks.
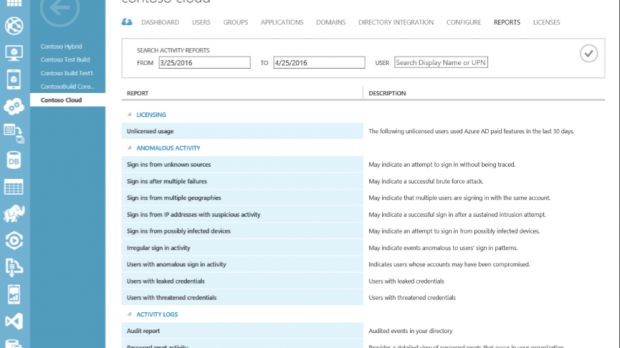
Microsoft says that there are two systems that help it catch and prevent most of the attackers from taking over accounts, even if they're using valid login credentials.
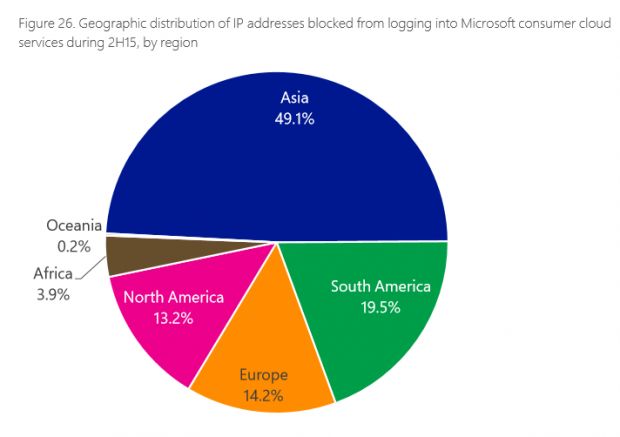
First off, Microsoft uses an incorrect password lockout system successfully prevents brute-force attacks, and then a location-based blocking feature doesn't allow attackers from accessing accounts from other parts of the world.
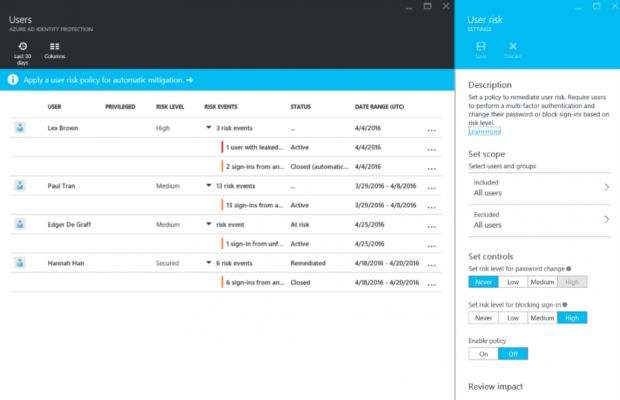
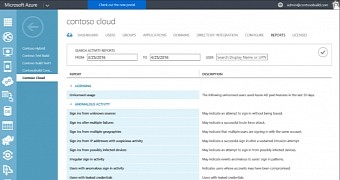
Additionally, for Azure Active Directory, administrators can also use the Identity Protection feature to create extra policies that require more authentication from incoming users, or they can decide to block any login attempt outright, based on a risk score assigned to each login operation.
"The capabilities [...] are combined with other protection algorithms, data feeds from the Microsoft Digital Crimes Unit and the Microsoft Security Response Center, phishing attack data from Outlook.com and Exchange Online, and information acquired by partnering with academia, law enforcement, security researchers, and industry partners around the world to create a comprehensive protection system that helps keep customers’ accounts safe," Microsoft writes in its report.
Nevertheless, this doesn't always protect online accounts, and the best way is for users to understand the dangers they're subjecting themselves to by not using stronger passwords or enabling a 2FA system when logging in.
For more insight on how Microsoft dealt with security threats in its other products, the company's 198-page Microsoft Security Intelligence Report Volume 20 is at your disposal.
 14 DAY TRIAL //
14 DAY TRIAL //