A new Android malware variant has surfaced, and it has rooting capabilities, can wipe your phone's storage, and boasts many other hidden capabilities that transform your precious phone into a zombie inside some hacker's botnet, Heimdal Security reports.
The way this malware spreads is unique, compared to other similar Android threats that rely on users installing apps from third-party app stores. In Mazar's case, users receive spam SMS/MMS messages with a link to a malicious APK (Android app file).
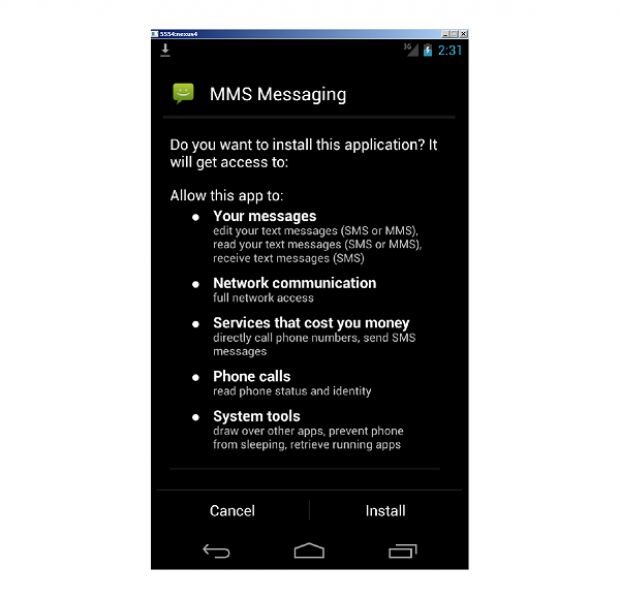
If the user falls for the spam and visits the link, they'll download the APK file on their Android. If they run it, they'll be prompted to install a new app.
This new app has a generic name, MMS Messaging, and also asks for admin privileges, which most inexperienced users will give it because of its name.
Mazar is packed full of intrusive functions
Once root access is gained, Mazar can do a lot of nasty stuff on your device, such as gain boot persistence to survive device restarts, send and read SMS messages, and call other numbers. Moreover, it can read the phone's state, inject itself into Chrome, alter phone settings, control phone keys, force the phone into sleep mode, query the network status, and access the Internet.
The more dangerous ability Mazar gains during this stage is the power to wipe your device's storage.
In their investigation, Heimdal's staff observed Mazar BOT downloaded a legitimate TOR Android app and installed it. With this app installed, the malware would be able to surf the Internet anonymously via the Tor network.
Mazar BOT may be run by a Russian cyber-gang
Once Tor is installed, Mazar will also send a message to an Iranian phone number with the message "Thank you." This message acts like a beacon and includes the device's location, letting the malware campaign's owner know when their virus has recruited a new bot device into their network or infected phones.
In some cases, Mazar also installed an Android app called Polipo proxy, which sets up a proxy on the device and allows the malware's owner to spy on Web traffic and carry out MitM (Man in the Middle) attacks.
Despite sending that SMS message to an Iranian phone number, the Mazar BOT source code includes specific instructions on how to stop the installation process if the phone is configured to use the Russian language.
This is a much better clue about the malware author's real location. It is an unwritten law in Russia that if cyber-criminals don't go after Russians, Russian authorities won't go after them.
The Mazar BOT was spotted for the first time last year by Recorded Future, being offered for sale on the underground malware market. This is the first case where Mazar has been detected in real-life malware campaigns.

 14 DAY TRIAL //
14 DAY TRIAL //