Security researchers from MalwareHunterTeam have stumbled upon a new type of ransomware infecting Web servers, and at this point, focusing on Magento shops.
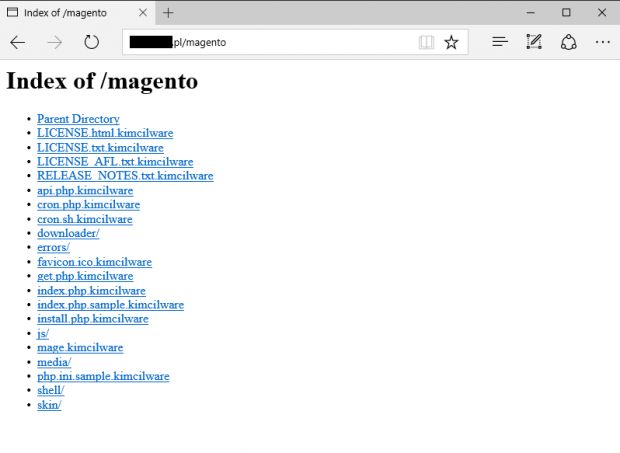
Called KimcilWare, the ransomware encrypts your Magento store files, appending the ".kimcilware" extension at the end of each file, rendering the store useless.
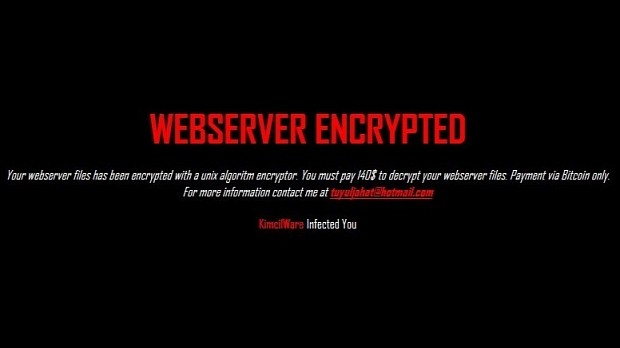
The ransomware also adds its own index file to the server, printing out a black page that replaces the store homepage, reading "Webserver Encrypted" as a headline in red, and then the ransom note that says "Your webserver files has been encrypted with a unix algorithm encryptor. You must paw 140$ to decrypt your webserver files. Payment via Bitcoin only. For more information contact me at [email protected]."
Infection mechanism yet unknown
We found less than ten Magento stores sporting this message until now (some mirrors here). The infection point is currently unknown, but there are two support topics that offer clues.
The first appeared on StackExchange on March 3 and is from a Magento store owner running version 1.9.1.0. The second appeared a few days later on Magento's official forum, from a store owner running version 1.9.2.4.
While in the first case the infection came out of the blue and affected only one site on a server with multiple Magento stores, in the second case, the store admin points the finger at the Helios Vimeo Video Gallery extension, which he believes was used to infect his site.
Possible tie to the Hidden Tear open source ransomware
Jack (@Malwareforme), a security research analyst, has found another ransomware called MireWare that sports the same [email protected] email address in its ransom note. From his analysis, MireWare is a variant of the Hidden Tear open source ransomware, known to have flaws in its encryption algorithm.
Based on an analysis from Bleeping Computer's Lawrence Abrams, the MireWare ransomware strain is currently broken due to the lack of a valid SSL certificate for its C&C server, but this could be very easily corrected.
As of now, Magento store owners should make sure they have strong passwords for their admin accounts and they should update to the latest Magento store versions as soon as possible or install all available patches for whatever version they are running.
The KimcilWare ransomware is only in its early stages of wreaking havoc among shop owners and still no in-depth details are known about its mode of operation. We will update the post with any new info or technical write-up that surfaces in the upcoming days. Below is an image of a Magento shop's files sporting the .kimcilware extension.
UPDATE: Bleeping Computer's Lawrence Abrams has discovered that the ransomware uses a Rijndael (AES) block cipher to encrypt files. Additionally Magento has informed us they took down the Helios Vimeo Video Gallery extension as a precaution at this time. We should clarify that KimcilWare is a Web-based ransomware that could theoretically infect any platform. The attacker behind this threat is apparently targeting Magento shops at this moment, but that doesn't mean it couldn't spread to other platforms.
UPDATE 2: We received an update via Twitter from @MalwareHunterTeam who informed us that 2-3 weeks after writing our story, Kimcilware has evolved to use a new ransom screen graphics, and that it still hasn't infected other types of platforms outside Magento. "It's clear now that their main target is Magento. They still can use it to attack sites with any CMS anyway, so we can't say only Magento, but the main is that," the researchers told Softpedia.
To clear the things: We aren't 100% sure that KimcilWare only targets Magento, but we found no evidence of that it's not. @piotrekkaminski — MalwareHunterTeam (@malwrhunterteam) March 30, 2016
KimcilWare is at 0/64: https://t.co/E0kb2h2iqz Not bad. :) @BleepinComputer @DanielGallagher @DanielRufde @Techhelplistcom @JAMESWT_MHT — MalwareHunterTeam (@malwrhunterteam) March 30, 2016
 14 DAY TRIAL //
14 DAY TRIAL //