A Tunisian hacker known as OussamiO has been busy for the past nine years distributing his Remote Access Trojan (RAT) via ads on the Dark Web, but also on popular networks such as Facebook, YouTube and Google's Blogspot.
Security experts from Trend Micro say OussamiO created the Lost Door RAT in 2007 and hasn't shied away from advertising his software on the public Internet, unlike many of his fellow malware developers who like to keep their operations hidden from prying eyes.
RAT coder is not afraid to market his product on the Surface Web
The main point of operation for OussamiO's activity is his Blogspot blog, where he regularly publishes about new Lost Door versions, upcoming updates, usage tricks and tutorial videos, which he brazenly hosts on YouTube.
Besides ads on the Dark Web on underground hacking forums from Brazil, China, and Russia, the crook is also very active on Facebook, where he runs his own page.
To buy his malware, users have to get in contact with him via email, either Yahoo or Gmail. The RAT's price is not publicly available, but similar tools usually sell between $10 and $50 depending on their capabilities.
Lost Door uses port forwarding trick to hide its activity
As for the RAT itself, Trend Micro says that security solutions may have a hard time detecting its activity because of the way it operates.
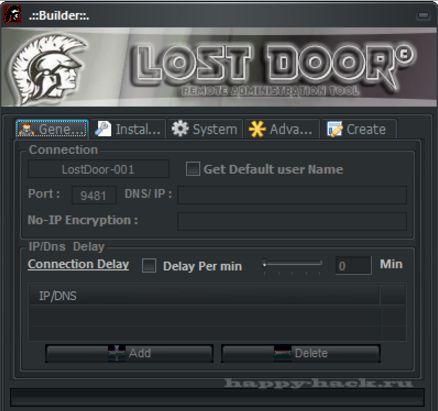
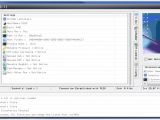
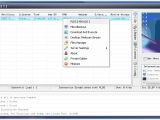
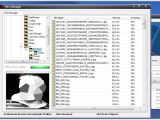
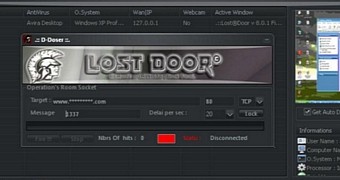
Lost Door comes with a builder, which means anyone that buys it has a plethora of options at his disposal to create a unique-looking and operating malware. The RAT's detection is also made more difficult because of the way it hides traffic.
"Lost Door leverages the routers’ Port Forward feature, a tactic also used by DarkComet. By abusing this feature, a remote attacker can gain access to the server side of a private network whether at home or in an office," Trend Micro's team explained. "This also means that any malicious traffic or communication can be passed off as normal/internal, thereby helping attackers mask their C&C address, since the server side does not directly connect to it."
Once Lost Door is deployed, an attacker would be able to access files, download and upload content from the computer, install and run any type of software, access webcam streams, log keystrokes, and virtually take control over the entire OS. OussamiO says he tested his RAT on all major Windows versions, from XP up to Windows 10.
What's more curious about this is that neither Facebook nor Google have taken down this crook's public pages after all these years.
 14 DAY TRIAL //
14 DAY TRIAL //