A threat group dubbed KingMiner uses a continually evolving cryptojacking malware known for targeting mostly Microsoft IIS/SQL Servers, with brute-force being the primary attack vector for compromising their victims.
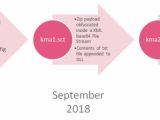
"The malware was first seen in mid-June 2018, and was rapidly followed by the deployment of two improved versions," said Check Point's Ido Solomon and Adi Ikan security researchers.
Moreover, "The attacker employs various evasion techniques to bypass emulation and detection methods, and, as a result, several detection engines have noted significantly reduced detection rates."
As detailed in Check Point's analysis, KingMiner makes use of a private mining pool for their crypto mining malware with the API disabled and the wallet not being used public mining pools to make sure that their activity is not being monitored.
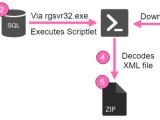
Once it manages to compromise the Microsoft Server machine it targets, the cryptojacking malware will search for previous versions of itself and upgrades them using up to date and architecture-specific malware payloads.
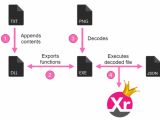
KingMiner's malware will download the payload in the form of an XML file which contains the ZIP file containing the binary as a Base64 blob to make sure that it avoids detection.
The malware went through multiple update stages since its discovery in June 2018
After expanding the ZIP containing the malware binary, an executable file contained within is launched starting up the XMRig miner it uses to illicitly mining Monero coins on compromised systems.
Even though the crypto miner is designed to use up to 75% out of the infected server's CPU resources, in practice, it goes up to 100%, probably because of programming errors.
Since it was discovered in June 2018, KingMiner's malware tool has gone through multiple stages of evolution, adding new detection bypass methods and new features while also showing evidence of code placeholders designed as footholds for new capabilities to be added in future updates.
"KingMiner is an example of evolving Crypto-Mining malware that can bypass common detection and emulation systems" concluded Check Point. "By implementing simple evasion techniques, the attacker can increase the probability of a successful attack."
A full list of KingMiner indicators of compromise including malware file hashes, hosts, mining pool and wallet addresses is available on Check Point's website.
 14 DAY TRIAL //
14 DAY TRIAL //