Security company Sophos warns of a new ransomware attack that uses a vulnerable Gigabyte driver in an attempt to break into a Windows system and then disable the running security software.
The attack is based on a security flaw found in 2018 in a Gigabyte driver and detailed in CVE-2018-19320. The driver, which has already been abandoned after Gigabyte acknowledged the bug, allows malicious actors to exploit the vulnerability in an attempt to get access to a device and deploy a second driver whose purpose would be to kill off antivirus products.
“This second driver then goes to great lengths to kill processes and files belonging to endpoint security products, bypassing tamper protection, to enable the ransomware to attack without interference,” Sophos explains.
“This is the first time we have observed ransomware shipping a Microsoft co-signed (yet vulnerable) third party driver to patch the Windows kernel in-memory, load their own unsigned malicious driver, and take out security applications from kernel space.”
Malicious driver
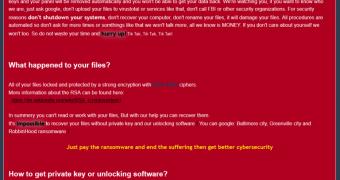
The used ransomware is called RobbinHood and requires victims to pay to unlock their files. If they don’t pay, the ransom note reads, the price increases by $10,000 every day.
The executable file used to exploit the Gigabyte gdrv.sys driver is called Steel.exe, and it extracts a file named ROBNR.EXE in the Windows temp folder, which in its turn extracts two different drivers, one developed by Gigabyte (the vulnerable one) and another one used for disabling the antivirus software on the compromised device. One the vulnerability is exploited, the Windows driver signature enforcement is disabled, allowing for the malicious driver to be launched.
Sophos says that nothing but the common practices to remain secure in ransomware attacks help you block the exploit, as even fully-patched computers with no known vulnerabilities can eventually be compromised.
 14 DAY TRIAL //
14 DAY TRIAL //