Security researchers at Sucuri, a company specialized in providing security solutions for website owners, have uncovered a nifty trick used by hackers who managed to hide a backdoor in one of the most innocent places, the Joomla CMS logo image.
The researchers found the backdoor in a previously infected website, which they were analyzing at that moment.
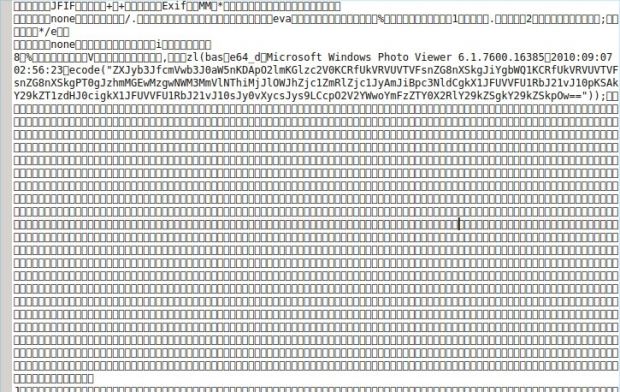
The backdoor was encoded in base64 and added to the Copyright field of the Joomla CMS JPEG logo image, inside its EXIF metadata header.
This image was normally displayed via the application.php file, where the hackers also modified the line of code where the logo was loaded, adding a function that made sure the image's EXIF data was being read and executed by the CMS.
While this made sure that the backdoor was executed on infected sites, it was also the telltale sign that gave the hackers away.
Unlike other cases where code was hidden inside images, in this particular case, attackers managed to embed their backdoor's code inside the JPEG file without distorting the final image.
This is not the first time security researchers find malicious code hidden in images.
In computer science theory, the technique of concealing data inside a picture is called steganography and has been used many times in the past. Some previous cases include the Stegoloader infostealer that hides in PNG files, and the Vawtrack banking trojan that hides in icon files.
 14 DAY TRIAL //
14 DAY TRIAL //