Google discovered an extensive iPhone vulnerability that allowed attackers to gain access to phones, including contacts, chats, databases, and live location data.
Researchers from Project Zero, a Google task force that has the only job of finding security vulnerabilities, discovered that iPhones were being hacked when a website injected an implant binary (malware), gaining elevated access to pretty much the entire phone.
The breath of the vulnerability is impressive because the attackers have been injecting malware and taking advantage of the iPhone’s weaknesses for at least a couple of years, and it was directed at particular communities.
The vulnerability persisted through OS updates
Project Zero determined that the websites which were injecting the malware had several thousand visitors each month. The team unveiled five separate, complete and unique iPhone exploit chains, which covered all versions starting from iOS 10.
All in all, 12 different vulnerabilities were found, seven for the iPhone’s web browser, five for the kernel, and two sandbox escapes. Google reported the problems back in January, and Apple issued a patch a few days later.
“There was no target discrimination; simply visiting the hacked site was enough for the exploit server to attack your device, and if it was successful, install a monitoring implant. TAG was able to collect five separate, complete and unique iPhone exploit chains, covering almost every version from iOS 10 through to the latest version of iOS 12. This indicated a group making a sustained effort to hack the users of iPhones in certain communities over a period of at least two years,” explained security researcher Ian Beer, Project Zero.
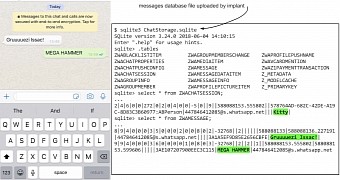
The implant monitored some of the more popular resources and apps, including the Yahoo mail app, Microsoft Outlook, Viber, Gmail, WhatsApp, Facebook, Skype, and a few others. Attackers also had full access to the chat databases from chat apps that use end-to-end encryption, to photos, contacts, live location, emails, and everything else.
The attacker’s implant could upload content every 60 seconds. What makes this even more interesting is that this attack took the form of a binary, which would not persist on the device after reboot. But the implant would be back when the user visited particular websites.
Even if the user reboots, the attackers already have the information, including user names and passwords for various services, even if they no longer have control. To make matters worse, the implant was discovered in the wild, which means that it was being used and it’s not just a theoretical exercise.
 14 DAY TRIAL //
14 DAY TRIAL //