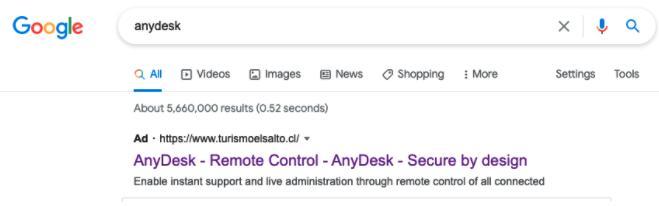
Cybersecurity experts announced on Wednesday the takedown of a clever malvertising network that targeted AnyDesk and delivered a weaponized installation of the remote desktop software via fake Google ads in search results pages.
The campaign, believed to be launched as early as April 21, 2021, contains a malicious file that masquerades as the notorious AnyDesk and, when executed, downloads a PowerShell implant to collect and exfiltrate system information.
Researchers from Crowdstrike said in a study that "The script had some obfuscation and multiple functions that resembled an implant as well as a hardcoded domain (zoomstatistic[.]com) to 'POST' reconnaissance information such as user name, hostname, operating system, IP address, and the current process name".
According to the company's website, AnyDesk's remote desktop access solution has been downloaded by over 300 million people worldwide. Although the cybersecurity firm could not attribute the criminal cyber activity to a single threat actor, it assumed it was a widespread campaign affecting a broad range of customers.
The PowerShell script has all the hallmarks of a typical backdoor, but it is during the intrusion route that the attack comes together and signals that it is more than just a routine data collection operation - the AnyDesk installer is distributed via malicious Google ads placed by the threat actor and then sent to unsuspecting individuals who search for AnyDesk using Google.
Users are misled into downloading fake infected AnyDesk installer
When visitors click on the bogus ad, they are sent to a social engineering page that is a clone of the authentic AnyDesk website and contains a link to the Trojan installer.
CrowdStrike estimates that 40% of clicks on the malicious ad led to the installation of the AnyDesk malware, with 20% of those installations involving hands-on keyboard behavior.
According to security researchers, "While it is unknown what percentage of Google searches for AnyDesk resulted in clicks on the ad, a 40% Trojan installation rate from an ad click shows that this is an extremely successful method of gaining remote access across a wide range of potential targets".
The company also said it notified Google of its findings, which reportedly took immediate action to pull the ad in question.

 14 DAY TRIAL //
14 DAY TRIAL //