In their attempts to hide from antivirus engines, hackers have altered the Fareit info stealer and malware downloading trojan to use a different file hash with every new infection, as Cisco's Talos team reports.
Fareit, a trojan specialized in breaching user computers, talking to a C&C (command-and-control) server, and then downloading nasty malware on their systems, has been around since 2012. While in the beginning it was a benign malware downloader, over time it has evolved into a talented information stealer, that's mainly specialized in extracting passwords from Web browsers.
We saw it stealing data from Fargo clients in 2013, and even earlier this year, when criminals were changing DNS entries to point unsuspecting users to servers where Fareit was hosted.
Fareit hides behind chameleon-like tactics
This time around, Cisco's Talos security team has stumbled upon a new version of this malware family that behaves like a chameleon, changing its file hash with each infection, even if the file name remains the same.
The first samples were seen in July of this year, and the malware's creators opted for this tactic to avoid hash- and signature-based detection methods.
"One possible reason for this might be, that the mechanism which they use to download additional malware files or modules (e.g. cclub02.exe), need fixed names or paths (like http://IP/cclub02.exe) and is not flexible enough to handle on-the-fly generated file names on a per victim/campaign base," explains the Talos Group's Earl Carter & Holger Unterbrink. "This could also indicate a pay-per-infection botnet, but of course, this is speculation until we reverse engineer the local binaries and analyze the server command and control software."
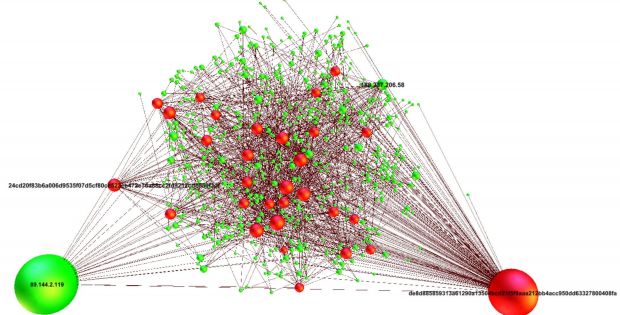
Around 2,500 Fareit samples detected, leading back to 2 IP addresses
Cisco's security products recorded 2,455 Fareit samples, but only 23 of them shared the same hash. Digging deeper into the data, they've also noticed that all these samples communicated with only 2 C&C servers, hosted at 89.144.2.115 and 89.144.2.119.
For most of the detected Fareit samples detection was low in VirusTotal, most of the binary files infected with the malware getting an average score of 4/56.
There was, though, one malware sample that got a score of 40/54, but that sample had been detected at the start of March 2015.
The evidence points that this campaign is run by the same group, and despite the cyber-criminals' effort to use different file hashes, Cisco's team says that a simple string match against the static file names should protect users from further infections.

 14 DAY TRIAL //
14 DAY TRIAL //